Description
Hi Sean,
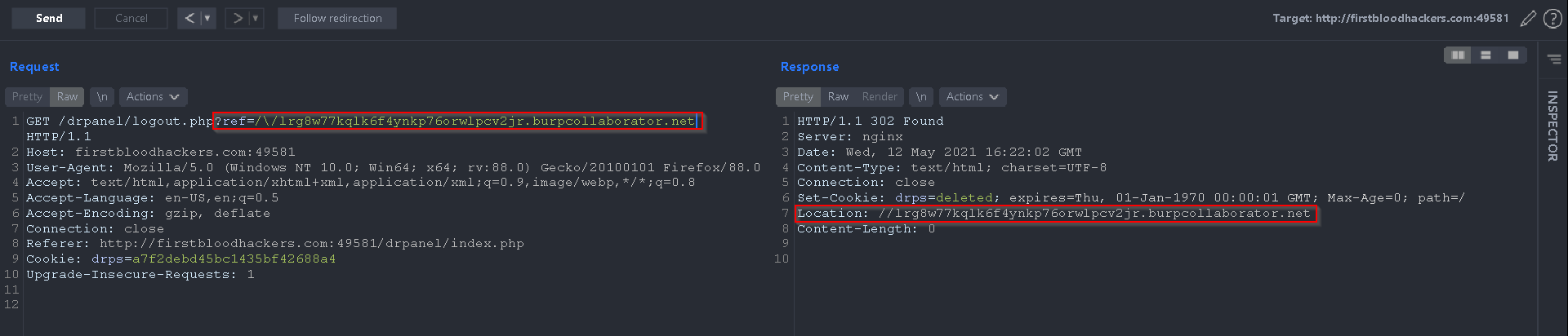
I just found out that there is an open redirect vulnerability on the /drpanel/logout.php endpoint using the ref parameter.
That enables an attacker to redirects the admin/users to the domain he wants.
Steps To Reproduce
There were some protections and filtering around the ref parameter, seems like // were filtered out and you would have been redirected to /, however, using /\/ I was able to bypass the filter and redirect the user to another domain
You can use the following payload to reproduce this redirect to your own domain:
/drpanel/logout.php?ref=/\/attacker.com
Impact
I wasn't able to find any SSO tokens or similar in the URL that could be potentially leaked using this open redirect, for now, the impact is just simply redirecting the user to another domain of attacker and doing phishing, however, keeping that in mind I will try to use that, later on, to bypass some protections over higher impact bugs such as SSRF.
Kind Regards,
HolyBugx
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 