FirstBlood-#231 — Stored XSS on Admn API endpoint for querying Appointment
This issue was discovered on FirstBlood v1
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-05-13, xnl-h4ck3r Level 4
reported:
Summary
A stored XSS payload can be entered into the First name or Surname fields on /book-appointment.html that can be fired by an Admin user visiting the query appointment API endpoint directly: /drpanel/drapi/query.php?aptid={APTID}
NOTE: THIS PAYLOAD ONLY WORKS IN FIREFOX AND CHROME BROWSERS
Steps to Reproduce
- Go to
/book-appointment.html and create a new apoointment setting the first name to <marquee onstart=confirm`XSS`>
- Sign is an the admin user.
- Use Burp to proxy traffic.
- On
/drpanel/index.php go to the appointment you made in Step 1 and click on the patients name to display the apppointment details.
- Go to Burps HTTP Histroy and copy the URL of the last GET request to
/drpanel/drapi/query.php. This will be something like /drpanel/drapi/query.php?aptid=56914781 where 56914781 is the appointment ID.
- When youy visit the URL, you will see an alert box displayed showing XSS
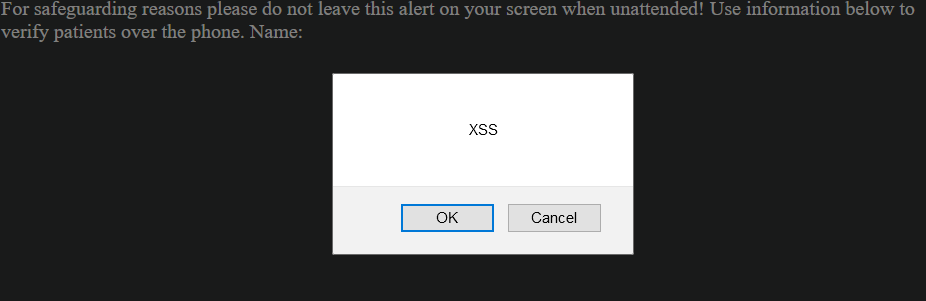
Impact
If stored XSS is possible then it can be possible for an attacker to leak the authentication cookie and log in as the admin user. The impact is lower because the victim needs to use Firefox or IE and has to visit the API url directly.
This report has been publicly disclosed for everyone to view
P2 High
Endpoint: /drpanel/drapi/query.php?aptid={APTID}
Parameter: fname, lname
Payload: <marquee onstart=confirm`XSS`>
FirstBlood ID: 10
Vulnerability Type: Stored XSS
When creating an appointment, it is possible to get stored XSS /drapi/query.php via the patients name
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 