FirstBlood-#43 — Doctor Registration code misconfiguration
This issue was discovered on FirstBlood v1
This report has been reviewed and accepted as a valid vulnerability on FirstBlood!
On 2021-05-09, vermsec Level 4
reported:
Hello team, The inviteCode parameter lacks proper validation, and allows us to register a user with other user's invite code which contradicts to what the application mentions about how the doc accounts are already created. This also allows us to use the same code to register multiple accounts.
Description
Business logic vulnerabilities are flaws in the design and implementation of an application that allow an attacker to elicit unintended behavior. This potentially enables attackers to manipulate legitimate functionality to achieve a malicious goal. These flaws are generally the result of failing to anticipate unusual application states that may occur and, consequently, failing to handle them safely.
Impact
Using this the attacker can register as many accounts as he wants.
Proof of Concept
Steps to Reproduce
-
A public post on reddit leaks an invite code for our application. link here - https://www.reddit.com/r/BugBountyHunter/comments/n4xzw1/firstbloodhackerscom_doctor_registration/
-
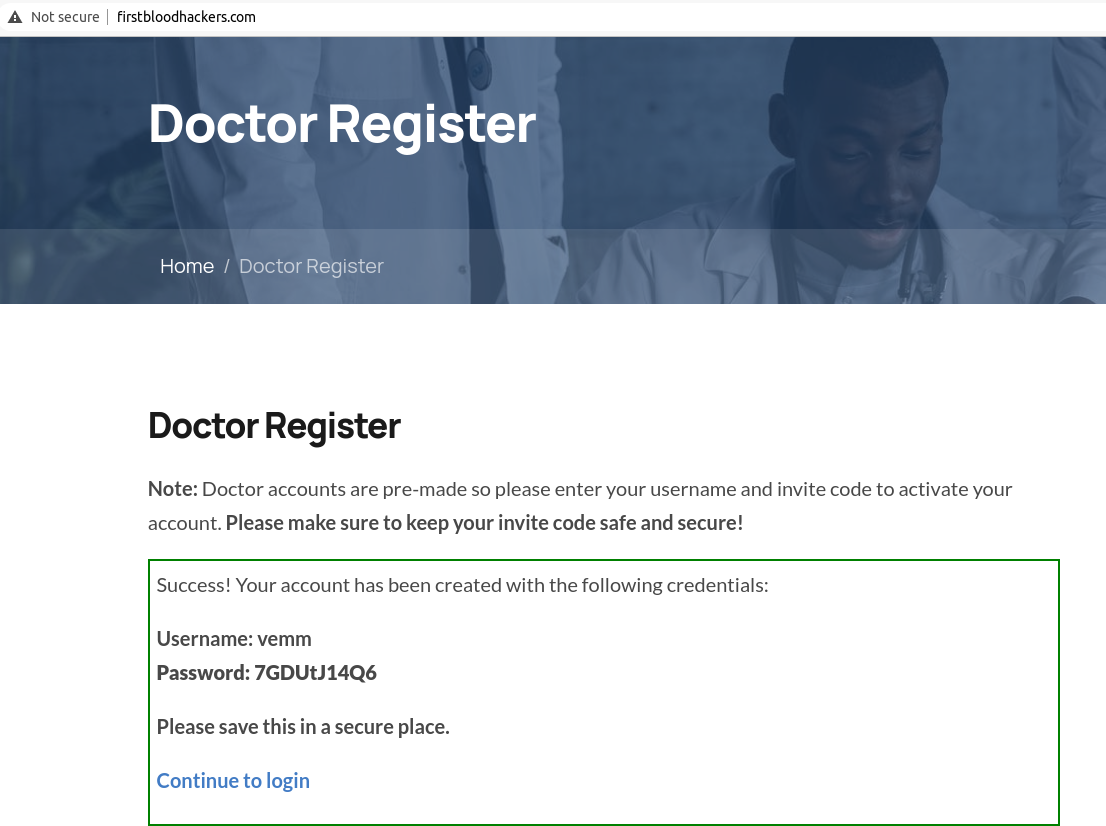
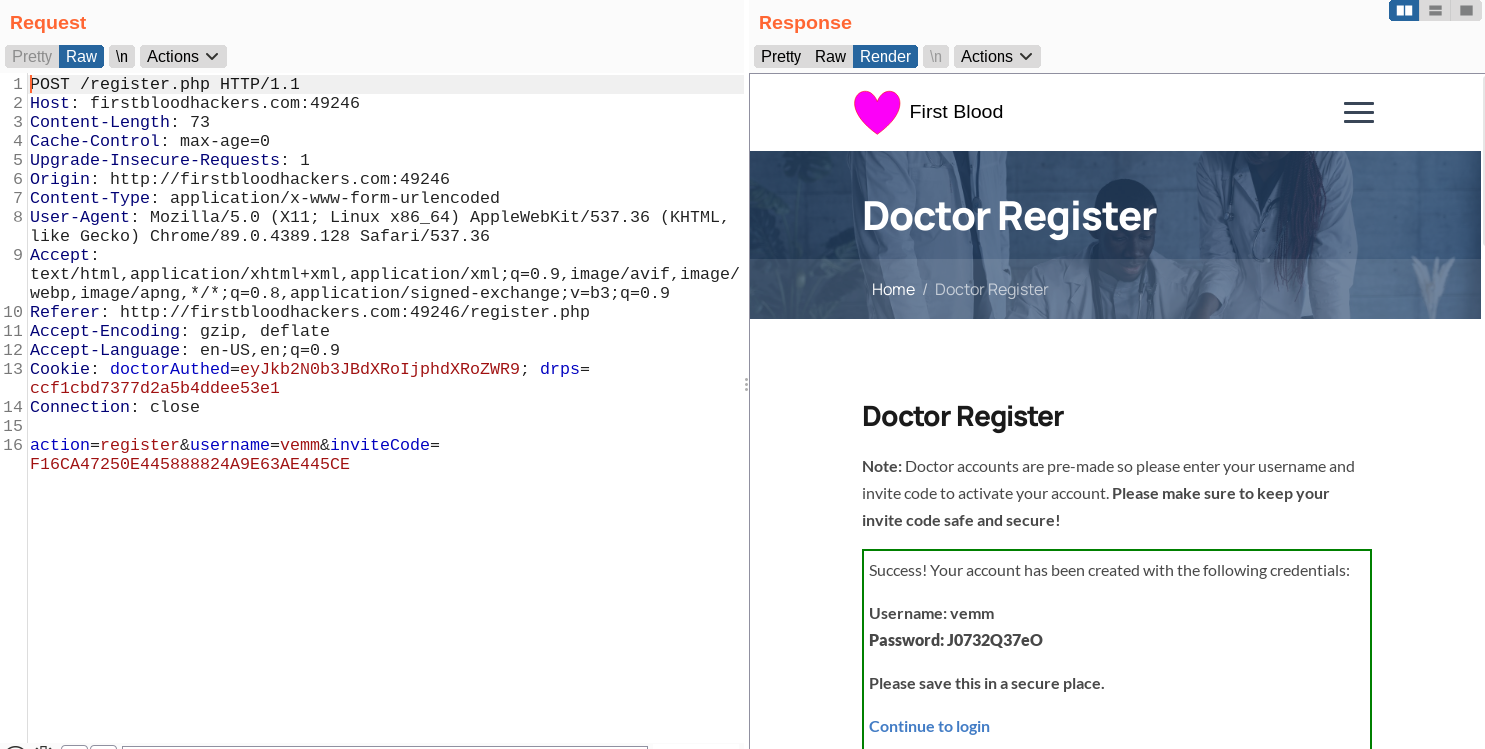
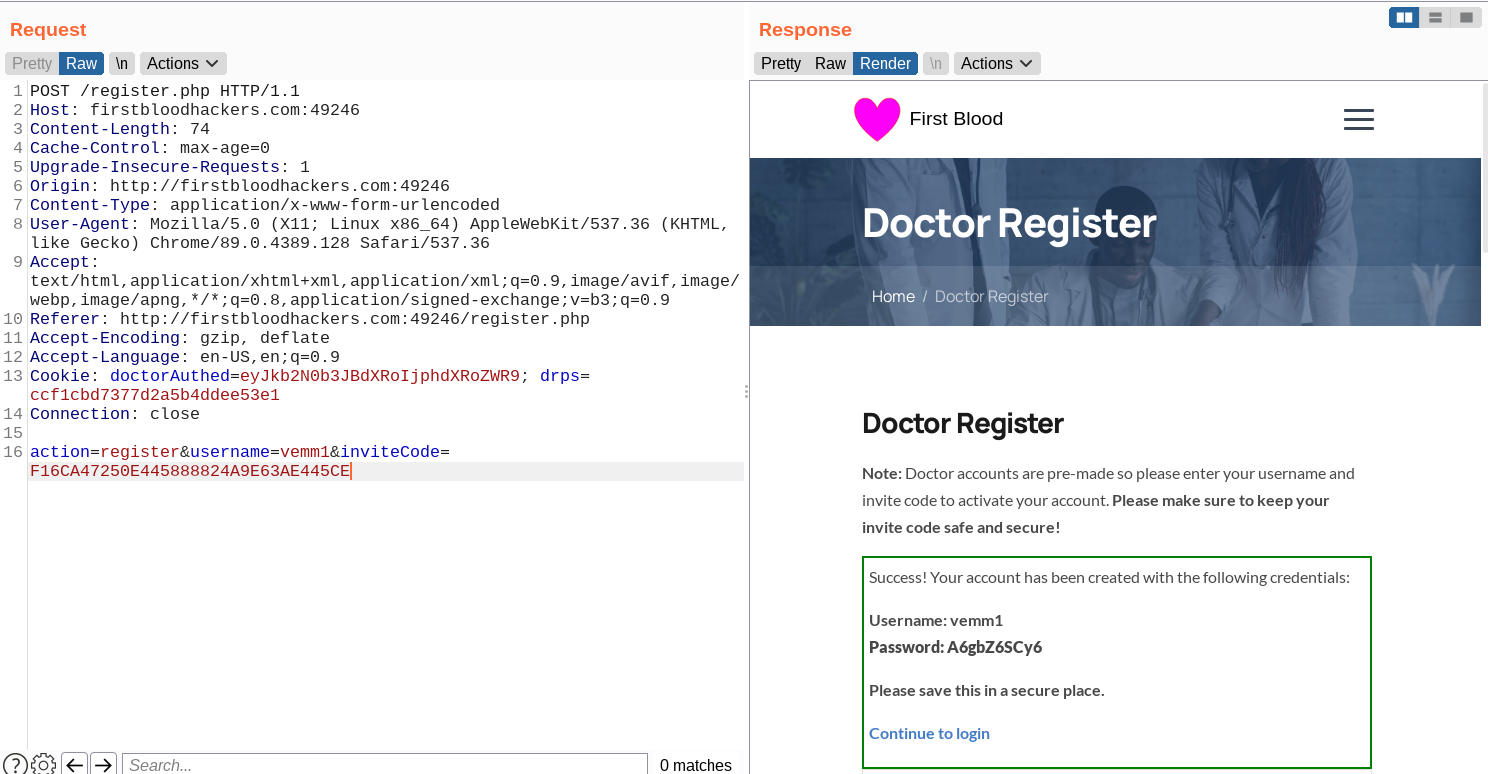
This code allows us to register a user, but the issue here is that the same code can be reused to register as many users as we want. As we can see in the following screenshots we are registering two users with the same invite code.
Remediation
Apply proper validation so that an Invite Code cannot be re-used.
This report has been publicly disclosed for everyone to view
P2 High
Endpoint: /register.php
Parameter: inviteCode
Payload: F16CA47250E445888824A9E63AE445CE
FirstBlood ID: 15
Vulnerability Type: Auth issues
A doctors invite code is leaked on the internet which if used grants anyone access to the doctor portal. The invite code should expire after use.
 Report Feedback
Report Feedback
@zseano
Creator & Administrator
Nice find vermsec and great report. Even though you weren't the first to find this, i'm awarding you a bounty at my own discretion. Great work again mate!
 Getting started
Getting started
 Test your knowledge
Test your knowledge
 Guides for your hunts
Guides for your hunts
 Useful Resources
Useful Resources
 Our community
Our community
 Endorsed Members
Endorsed Members
 Hackevents
Hackevents
 Member Articles
My BARKER Experience
Member Articles
My BARKER Experience
 Learn about vulnerability types
Learn about vulnerability types  Getting started in bug bounties
Getting started in bug bounties  Free Web Application Challenges
Free Web Application Challenges ZSeano's Methodology
ZSeano's Methodology Effective Note Taking for bug bounties
Effective Note Taking for bug bounties Disclosed HackerOne Reports
Disclosed HackerOne Reports 


 Report Feedback
Report Feedback